Ransomware Protection 101: Everything You Need to Know
This guide will explain what ransomware is and how you can protect yourself and avoid becoming a ransomware victim.
Ransomware is a malware designed to encrypt the files in a computer or mobile system to make them inaccessible to legitimate users.
If attacked, it demands a ransom from the victim to decrypt the files and restore the system to its original state. It gives the victim instructions to pay the ransom, often a large amount of money that must be paid as untraceable bitcoin transactions.
If the victim does not adhere to the rules, the victim can even be threatened by them to leak the sensitive data to third parties for illegal purposes.
Ransomware is all over the world, evolving with new variants frequently. Any computer system which does not have adequate preventive measures is vulnerable to ransomware attacks.
The attacker then demands a ransom in exchange for decrypting the files and restoring the system to its normal state.
To launch an attack, cybercriminals first identify and gather information on potential targets, looking for security weaknesses in their computers and networks.
They use various methods to infiltrate systems, including phishing emails, spear-phishing campaigns, drive-by downloads, infected removable media, and exploiting vulnerabilities in remote desktop protocol (RDP) ports.
Once inside, the ransomware disables backup files to prevent data recovery, then encrypts the system’s files. The victim is notified of the compromise and given instructions to pay the ransom for the decryption key.
However, even when the ransom is paid, some victims report being unable to recover their files, losing both their money and data. Additionally, the stolen data is often sold on the dark web.
How does Ransomware Work?
Ransomware attackers plan the execution by identifying potential victims, collecting their information, and analyzing the security vulnerabilities of victims’ computers and networks.
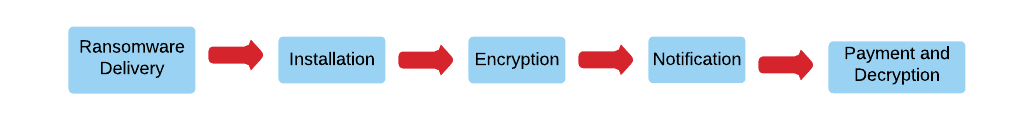
Typically, ransomware goes through 5 phases, from infection to decryption, which we will explain in more detail.
1. Ransomware delivery
For ransomware to get into a system, attackers must manipulate the victim to execute a certain action. There are several entry paths attackers use for this purpose.
First, attackers devise how the ransomware gets delivered into the target system. First, attackers plan how the ransomware gets delivered into the target system.
How Ransomware gets delivered into a system?
| Ransomware Delivery Method | How ransomware gets delivered through this method? |
| Phishing | Victims receive emails or messages in social network chats with a malicious link or attachment like a pdf document which appears to be unharmful. Once the user clicks on the link or opens the attachment, the ransomware gets delivered into the system. |
| Spear Phishing | Attackers who disguise themselves as trustworthy sources send malicious emails to specific individuals or businesses. They use personalized messages to cleverly persuade the victim to execute the action and inject the ransomware. For example, the sender may be disguised as your help desk asking you to change the password if not you will lose access. Even the most knowledgeable person could fall victim to such emails. |
| Drive-by Downloads | Attackers compromise a web page using ‘exploit kits’ that embed malicious codes. When the victim visits that page, the malicious code runs and silently scans the visiting device to identify any security gap. If found, the exploit kits launch the exploit and download the ransomware. |
| Removable Media | USBs can come as promotional gifts that may contain ransomware inside them. Once plugged into a device, ransomware will deploy into the computer. |
| Exposed Remote Desktop Protocol (RDP) Ports | Once RDP ports are open to the internet, it is vulnerable to cyber-attacks. Attackers scan for exposed RDP ports and use stolen credentials to log in. Once it gains access, disable security systems and deliver the ransomware payload. |
2. Installation and execution
After ransomware gets delivered into a system, installation and execution begin. During this phase, It will identify backup files in the system to prevent data restoration using backups. Some ransomware uninstalls security software in the system before its installation.
3. Encryption
The private key, the decryption key, is only known by the attacker. The private key, the decryption key, is only known by the attacker.
Then it will do the real damage to the system, encrypting the system files. It uses a military-grade encryption method like Asymmetric Encryption, which is impossible to crackSome ransomware in this phase can infect the Master Boot Record (MBR), completely blocking access to the system. (However, keep in mind that there are types of ransomware that do not encrypt files which we will discuss in the ransomware types section).
4. Ransom notification
After completing the encryption routine, it will display a message to the victim that they have been compromised and should pay money to decrypt the files.
Sometimes, it will ask the victim to read a file to know how to pay them. Usually, attackers request to pay the ransom as a cryptocurrency because it is difficult to track.
Decryption after the ransom payment
When the ransom is paid, the attacker will provide the decryption key to unlock the encrypted files. However, there are cases where companies have been unable to recover the data with the encryption key, permanently losing both the money and the data.
Most often, stolen data will be sold on the dark web.
Should You Pay the Ransom?
The decision to pay or not pay for the ransomware depends on how critical and urgent the data is. Sometimes, the decision to pay the ransom may be the worst idea because news by Kaspersky revealed that over half of the victims pay the ransom, but only a quarter of victims were able to get their data returned.
Therefore, paying the ransom does not guarantee you will get your data back. Paying the ransom also encourages cybercriminals to continue these attacks.
Consequently, you should, by all means, refrain from paying the ransom and instead report the responsible parties about the attack and take action under their guidance.
Who is Responsible for Ransomware Attacks?
Who is behind ransomware attacks, and is money their only motive? As discovered by cybersecurity investigators, there are two types of perpetrators behind ransomware attacks.
They have different motivations behind the attack and typically are experts in hiding their real identity.
Organized cyber-criminal gangs
Organized cyber-criminals are well-equipped with all the necessary tools and technologies to plan attacks and find potential targets.
They are a network of cyber criminals who make ransomware a profession. They have automated strategies to run the attacks, handle ransom payments, and the decryption process.
They manage to hit several victims in a single attack, typically asking for only smaller ransom payments from each victim. Terrorist groups may even back some to launder money for terrorist activities.
Cyber-criminals lead by states
There have been reports that countries like North Korea, Russia, and Iran, which have sanctions imposed by foreign governments, are behind ransomware attacks. Their intention is not just to steal money butto createg havoc within countries as revenge against their adversaries. For example:
- SamSam ransomware attack in 2018 was allegedly led by two Iranian hackers.
- NotPetya was led by the Russian military intelligence arm.
- Wannacry attack was led by a North Korean cybercriminal group called ‘Lazarus’. There are several reasons like lack of clear decryption, using only three payment addresses, and lack of communication with the victims, which we can suspect its real motive is not the financial gain.
Ransomware Targets
Ransomware attackers target systems with data that is critical and sensitive. They target both big and small businesses alike. If the data needs immediate access, then there is a possibility that the victim would agree to pay the ransom quickly.
They also target organizations having outdated security systems with vulnerabilities and poor security practices. Here in this section, we will identify the top 3 targets of Ransomware that often fall victim to them.
Healthcare
Health care facilities store medical records critical to patients and require immediate access to them. Otherwise, it can be life-threatening to the patients. Wannacry ransomware, for example, impacted the UK’s National Health Service in 2017, forcing them to cancel surgeries and appointments and relocate emergency patients.
News reports say that, because of the attack, the NHS had to cancel 19,000 appointments, upgrade IT systems and carry out cleanup, costing them 92m pounds.
Education
Educational institutions like universities, schools, and colleges have sensitive research data, intellectual property, and staff personal and financial records.
They often lack strong cybersecurity principles due to budgetary constraints. Most students lack the proper knowledge of cyber-attacks and riskily engage with the network.
Thus, they are particularly vulnerable to cyber-attacks. For example, in 2016, The University of Calgary paid $20,000 in bitcoin to ransomware that attacked its computer system. In particular, the education sector has seen a surge of ransomware attacks due to the increase of online learning.
Government agencies
Government agencies, particularly security departments, handle sensitive public information like military and criminal information.
Such agencies need to take immediate action if a data breach happens and are willing to pay the ransom to restore the attacked system as quickly as possible.
Furthermore, they then outsource private companies for certain services. Ransomware can target such third parties to infiltrate governments’ critical infrastructure.
Apart from the business falling under the above categories, Ransomware has targeted the following sectors.
- Retail and Finance
- Utility Companies
- Multimedia providers
- HR departments
- Mobile devices
- Cloud computing providers
- Law firms
- Oil and energy firms
How to Avoid Ransomware
From a ransomware attack until you recover, the damage could be financially and emotionally unbearable. Therefore, drive your focus on ransomware prevention in the first place because prevention is the best defense against ransomware. In this section, we will discuss 10 ways to prevent ransomware from injecting into your system.
Ransomware prevention methods
- Refrain from clicking on suspicious links and opening unsafe attachments – Phishing Refrain from clicking on suspicious links and opening unsafe attachments – Phishing emails can be from senders disguised as law enforcement agencies, accounting firms, or your close acquaintances. Always check the email address and sender information. If you receive private messages from unknown people or close acquaintances containing links, always check with the sender to confirm its legitimacy.
- Avoid exposing personal information – To get into your system, ransomware can collect your information. They can be searching through your social media profiles to identify key information. Thus, do not overexpose your personal information unless necessary.
- Keep the operating systems and software up-to-date – Make sure the Operating system(OS) and software are in the latest version allowing automatic updates. OS updates not only contain the latest features but also contain security patches for any security flaws in the system.
- Maintain regular backups – Keep backup copies of the files, particularly the most important files and store them outside your network in multiple locations. Because as mentioned earlier, ransomware targets backups inside the system. Cloud platforms are ideal for keeping backups because they are equipped with state-of-the-art backup and recovery technologies.
- Download from trusted sites – Refrain from downloading software from untrusted sites. Always check for the URL and visit sites that only have HTTPS in the URLs or have lock seals in the address bar. Be extra cautious when downloading free software and games.
- Provide necessary security training – Make the users of your system aware of the causes and actions of ransomware. Educate your users about best practices and rules they should adhere to avoid such malware attacks by conducting regular security awareness training. This training should include ransomware phishing simulation to identify users who need more training on cybersecurity.
- Configure Email protection – spam filtering to identify most common ransomware file types like .exe, .vbs and .scr. Scan and monitor the emails circulating in your system using secure email gateways, which can block phishing attacks. You should also use encrypted email services such as ProtonMail.
- Use anti-ransomware software – This software is designed to identify malware, including ransomware. They have light-eight anti-ransomware tools that scan your pc regularly and remove if ransomware is located. For personal PCs, there is free anti-ransomware software available.
- Use endpoint protection – Certain traffic could be prone to ransomware. Endpoint security solutions provide the security for the entire corporate network with all the endpoints connecting to it. It can protect your device from such ransomware-prone traffic entering your PC.
- Define Access Control – Use the principle of least privilege where your system users are given the minimum level of permissions. Only users with higher privileges can only access and manipulate sensitive data in the system.
Different Types of Ransomware
All the ransomware that has been identified so far falls into two categories: Crypto-Ransomware and Locker Ransomware.
Crypto Ransomware and Locker Ransomware
Crypto Ransomware
Crypto ransomware typically infiltrates the victim’s computer system and encrypts files using a strong encryption method. It usually does not lock down the system. Victims can still access the unencrypted parts.
Locker Ransomware
Locker ransomware locks and shuts down the victims’ computers. This ransomware usually does not penetrate the whole computer system or encrypt the files. Sometimes the users may even find that their mouse or keyboard is frozen and only allows iterating with the ransom window.
Popular Ransomware Types
| Ransomware Type | Delivery Method | Features |
| CryptoLocker | Phishing email attachments and through the peer-to-peer botnet Gameover Zeus | Created in 2013 used asymmetric encryption to encrypt files. Its ransom note warned the victims that the key would be deleted unless they paid the ransom. Victims were required to get the private key to decrypt the files through an online service. It was completely shut down in 2014. |
| CryptoWall | Malicious pdf attachments and exploit kits in infected websites | It encrypts files and scrambles the file names making it harder for victims to identify them. There are multiple variants of cryptowall, including CryptoWall 3.0, CryptoWall 3.0, and CryptoBit. |
| Jigsaw | Malicious attachments in spam emails | One of the most destructive ransomware types which progressively delete the encrypted files to persuade the victim to quickly pay the ransom. Within 72 hours, it will delete files per hour. After 72 hours have passed, if the ransom is not paid, it will delete the rest of the encrypted files. |
| GoldenEye | Microsoft SMBv1 Vulnerability | Appeared in 2017 and heavily struck a lot of Ukrainian companies. It not only encrypts files but also encrypts the Master Boot Record (MBR), completely blocking access to the computer. |
| Locky | Spear phishing emails with a word document attached. | The word document contains malicious macros. When the victim enables the macro, it downloads the ransomware and begins to encrypt the files. |
| WannaCry | Through the EternalBlue developed by the National Security Agency (NSA) for older Windows versions | Released in 2017, this ransomware targeted Windows Operating Systems. Contained multiple components – initial dropper, encryptor, and decryptor. It exploits a vulnerability in Microsoft’s Server Message Block (SMB) protocol. |
| BadRabbit | Drive-by download – masquerading as an Adobe Flash Installer in compromised websites | BadRabbit first emerged in 2017, infecting companies in Russia and Eastern Europe. Attackers have demanded to pay 0.05 bitcoin, which amounted to $285 within 40 hours of the attack. |
| Cerber | Phishing emails, infected websites, and ads | Cerber is a ransomware-as-a-service that licenses the ransomware and provides it to other cyber attackers in exchange for a percentage of ransom. It appeared in 2016 and targeted Millions of Office 365 users. |
| Crysis | Phishing emails with double file extensions, legitimate software, and through Windows RDP Protocol | Uses both AES-256 and RSA-1024 encryptions applied to fixed, removable, and network drives. |
| CTB-Locker aka Curve-Tor-Bitcoin Locker | Emails with an infected .zip file attached | Uses elliptic-curve cryptography (ECC) to encrypt the files in the victims’ hard drive. First infected in 204 attackers have demanded higher ransom payments for CTB-Locker when compared to other ransomware. |
| KeRanger | Infected Installer called Transmission | Appeared in 2016, successfully infected Mac Computers remotely executing on the victim’s computer. |
Major Ransomware Attacks
Ransomware has impacted a lot of organizations in different countries. According to cybersecurity statistics, attacks are estimated to cost $6 trillion annually by 2021.
Let’s discuss the most prominent and impactful ransomware attacks that have happened so far and how they have impacted the organizations financially.
Check out our main list of the biggest ransomware attacks in 2021.
WannaCry Ransomware Outbreak
This is known as the most devastating ransomware attack history has ever seen. It was launched in 2017 and targeted Microsoft Windows computers worldwide, particularly Windows systems which have not installed Microsoft security updates after April 2017.
According to published reports, it has attacked over 200,000 computers in 150 countries, causing them to lose billions of dollars.
The most impacted countries include Russia, Ukraine, and India. Affected organizations include National Health Services(NHS) in the UK, Honda, Hitachi, Universities in China, and state governments of India.
The USA and UK suspect North Korea is behind the attack. The kill stopped the spreading of the Wannacry switch developed by the researcher Marcus Hutchins and the release of emergency software patches by Microsoft.
University of California Ransomware Attack
Netwalker is a ransomware gang that attacked the University of California in San Francisco, one of the leading research institutions working on covid-19 pandemic research, in June 2020.
The reports revealed that the university had to pay $1.14 million in bitcoin to the attackers to recover the data, which was a negotiated amount to the original ransom of 3 million us dollars.
The Ransomware encrypted files on several servers in the IT environment of the school of medicine. This can be seen as one of the opportunistic attacks because the encrypted data are related to covid-19 vaccine research, which was critical at that time.
The university reported that they agreed to pay the ransom as the data is important for them to continue the academic work they pursue.
Ryuk Ransomware Attacks
Ryuk has successfully attacked high-profile organizations like Los Angeles Times and Tribune newspapers, Universal Health Services (UHS) hospitals, and an IT consulting company in Paris.
Once shot, it disables Windows restore features and shuts down services and processes. It is behind some of the highest ransom demands, like 5 million to 12.5 million US dollars.
It appeared in 2018; it is first believed that the Russian cyber attackers known as Wizard Spider are behind Ryuk ransomware. But most recent investigators have identified two Russian criminals behind the attack.
Petya and NotPetya Attacks
Petya and Not Petya ransomware variants initiated their propagation in 2016 and 2017, primarily through phishing emails with malicious attachments.
Reports estimate that different variations of Petya have caused around 10 billion US dollars since its inception. Petya specifically targets systems with Windows operating systems infecting the MBR. It means that it blocks the operating system entirely.
While NotPetya targeted Ukrainian companies like the Chornobyl Nuclear power plant, Petya has affected different organizations worldwide.
For example, Heritage Valley Health System USA, oil companies like Rosneft, Russia, and food companies like Cadbury Chocolate Factory Hobart.
Apart from these most notable ransomware attacks, Conti, Maze, DopplePaymer, and Revil are top ransomware to the lookout in 2021 that could become outbreaks.
Summary
In this guide, you will learn everything you need to know about ransomware, including the most common types and widespread attacks that have happened so far worldwide. Ransomware is a powerful weapon that continues to harass the world.
If a ransomware attack happens to a system that stores sensitive data critical for a business to continue its operations, it can entirely cripple.
Consequently causes severe financial losses and damages to the company’s reputation. Therefore, use the prevention techniques described in this guide to secure your system from ransomware attacks.