NoName Attacks NATO
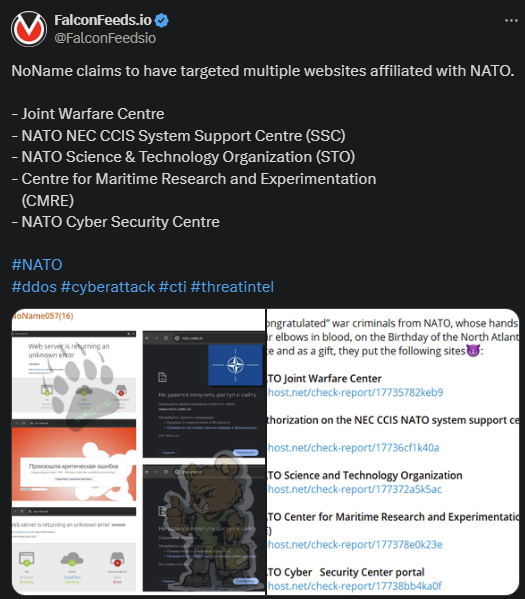
Infamous pro-Russian NoName targeted multiple websites affiliated with NATO. This includes the Joint Warfare Centre and the NATO Cyber Security Centre. The attacks have been confirmed, but it’s unclear how severe they’ve been.
- NoName posted a note following the hits, mocking NATO members and calling them “war criminals”
- The note also showed the target websites that went offline as a result of the DDoS attacks
- NoName is an infamous pro-Russian cybercriminal organization that uses cyber-attacks to push its political and ideological goals
- This isn’t the first cyberattack that had NATO as its victim, as the organization has been hit multiple times in the past
Some of the attacks that targeted NATO even resulted in leaked documents showcasing the organization’s strategies and military planning. While these weren’t necessarily classified documents, they weren’t meant for the public eye either.
While this recent attack didn’t result in any leaked documents, at least based on the evidence we have so far, it is concerning nonetheless. The attacks show that NoName is not only capable of such high-end intrusions but also fearless.
The pro-Russian gang has targeted numerous anti-Russian establishments since the beginning of the Ruso-Ukrainian war. And their tactics haven’t stopped there.
Since its inception, NoName has resorted to a variety of tactics to intimidate its targets, including DDoS attacks, spreading misinformation, sending threatening letters, etc. These tactics paint NoName as a highly versatile and resourceful gang.
The fact that NoName targeted and managed to breach NATO websites reinforces that idea. In fact, the organization appears to be so powerful and influential that some have linked it to the Russian government itself.
No clear evidence has confirmed this theory so far, though.
What Was NATO’s Response to the Attack?
So far, it’s unclear what measures NATO has chosen to adopt following the attack. And nobody from NATO’s side has come forth with any clear statement. When it comes to an actual response, things are easier said than done.
NoName has been active since March of 2022 and it has never been threatened so far. That’s not because it hasn’t been targeted but because it managed to evade anyone who tried to crack down on it.
This is for several reasons, including the fact that NoName often collaborates with other pro-Russian gangs like Killnet and Xaknet. These take some of the heat off of NoName operators, helping them to cover their tracks.
NoName also uses affiliates to cause chaos and create even more false leads for law enforcement agencies to waste time on. Finally, this is a very well-funded, powerful, and influential cybercriminal gang.
It can reorganize very fast and cover its tracks with extreme efficiency and precision. Anonymous whistleblowers have hinted at NoName operating in a military-like style. The hackers have strict deadlines they need to meet.
They also work around the clock and are required to highlight and breach at least 5 and up to 15 targets or more per day. This explains why NoName always posts their victims in batches; because they always attack several at a time.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

