NoName Enters Day 9 in Ukraine
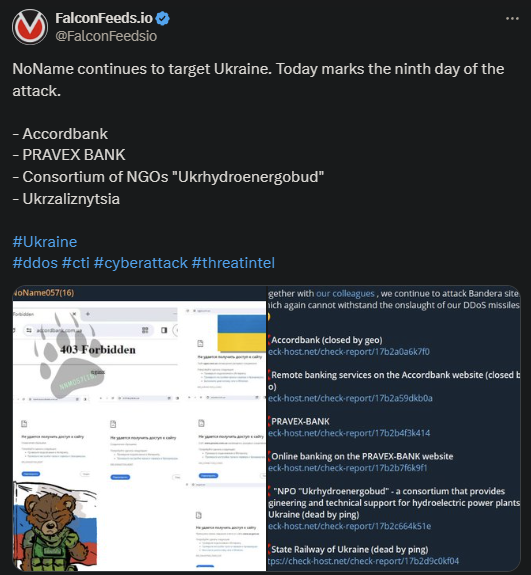
NoName operators continue their Ukrainian offensive, entering their 9th consecutive day. The hackers have hit Ukraine’s infrastructure with numerous DDoS floods, causing several victims along the way. Today’s attack targeted 4 more institutions.
- The hackers breached Accordbank, PRAVEX BANK, Consortium of NGOs, and Ukrzaliznytsia, which provides technical support to hydroelectric plants
- NoName posted the evidence of the attack on their public website, mocking the target’s defensive capabilities and showing images of the “dead” websites
- NoName is the most vocal pro-Russian cybercriminal gang that has been active since March 2022
- The NoName gang qualifies as the most active organization today, capable of carrying multiple attacks per day
Ukraine has been the target of numerous cyberattacks since the beginning of Russia’s invasion and before that. Many of these have been performed by pro-Russian organizations like Killnet, Xaknet, NoName, Anonymous Sudan, and many others.
The typical attack revolves around using DDoS botnets to disable the target’s website and impact their services. These types of attacks have proven to be very effective against most targets, often taking their websites out for weeks.
But that’s not the only method of attack NoName uses.
The pro-Russian gang made its intentions and affiliation known since March 2022, shortly after it hit the public sphere. NoName hackers have essentially declared war to everyone affiliated with Ukraine or who expresses anti-Russian views.
They then conducted operations against both Ukraine and its allies, often producing multiple victims per day. The gang has resorted to several MOs, including DDoS attacks, extortion, blackmail, and even threatening letters.
What Do We Know About NoName?
The shortest and most honest answer would be ‘not much’. NoName has emerged literally overnight, shortly after Russia’s invasion of Ukraine. The gang first made itself known in March 2022 and became active immediately after.
NoName’s activity level has increased dramatically, with the hackers often hitting multiple targets per day with no day off. They also seem able to penetrate high-value governmental institutions with relative ease, with no hesitation or fear of repercussions.
This hints at solid funding and support from unknown benefactors. Not much is known about NoName’s internal structure and operations, but some people have suggested affiliations with the Russian government itself.
This hasn’t been confirmed yet and it’s unclear whether NoName actually needs that. The group often relies on affiliates to conduct some of its operations, which allows the gang to cut off on expenses and limit their exposure in the process.
NoName also often collaborates with other pro-Russian cybercriminal groups for the same reasons. The same appears to be the case today, according to the hackers’ own post.
NoName mentioned conducting this latest operation in collaboration with some of their allies, although they don’t name them. But one can deduce some of the missing names, including the Russian Cyber Army.
The latter was involved in a previous attack in collaboration with NoName, during which multiple Ukrainian targets were hit. These strategies make NoName one of the most feared and resourceful pro-Russian gangs today.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

