NoName Visits Moldova Again
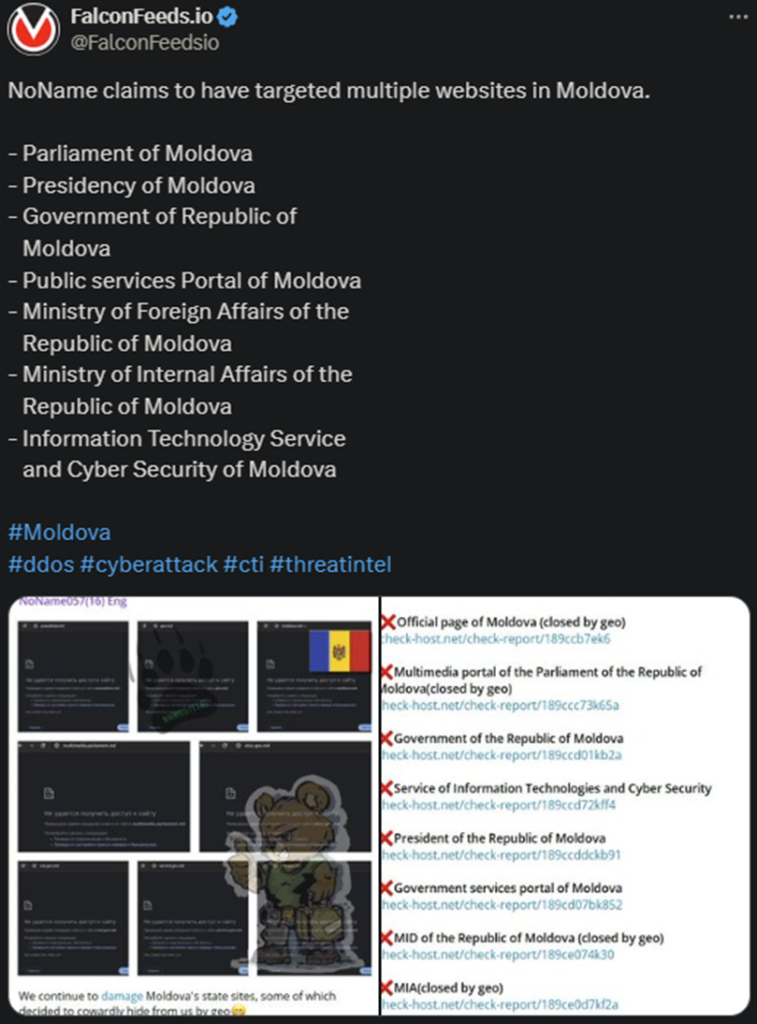
After taking a short break, during which it diverted its attention at other targets, NoName resumed their “Moldovan operation.” The hackers hit Moldova again, this time breaching 7 high-profile targets.
- Among the institutions being hit, the most notable ones include the Parliament, the Presidency, and the Ministries of Foreign and Internal Affairs
- NoName published the evidence of the attacks with a note attached that mocked Moldova’s cybersecurity and defensive attempts
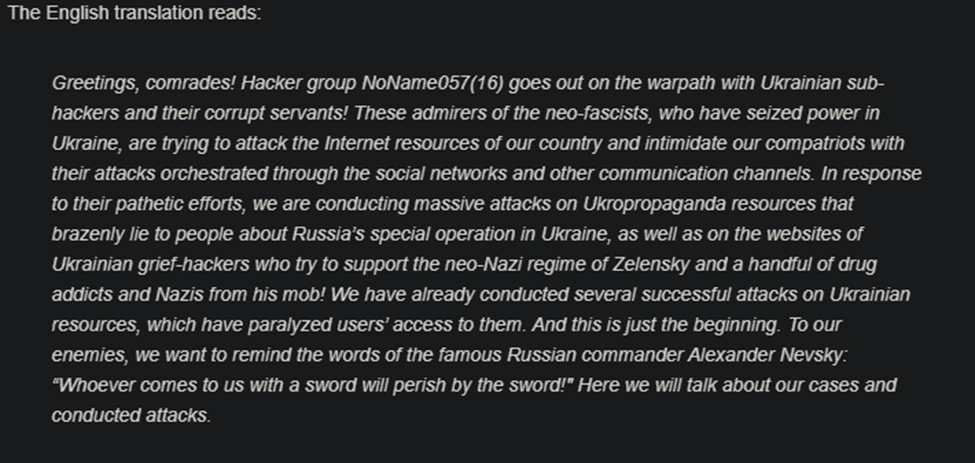
- According to the hackers themselves, these attacks are strictly fueled by Moldova’s willingness to support Ukraine during the ongoing war
- NoName is the most vocal supporter of the Russian regime, as they continue to target its enemies, along with their supporters
As NoName’s note suggested, Moldova’s cybersecurity experts took measures to shield the potential targets from any potential attack. Some of the attempts were successful, but some were not. It’s unclear how much damage the hackers managed to inflict.
NoName operators rely on standard DDoS botnet attacks to overwhelm the target system and take it offline. While these attacks are fairly common, they can sometimes produce unexpected damages, depending on the target’s level of preparation.
In some cases, such DDoS incursions have disabled the victim’s website for weeks, causing meaningful financial and logistical problems and losses.
But this isn’t necessarily NoName’s goal. Instead, the organization aims to disrupt, intimidate, and discourage the victims from pursuing their goals. Which, in all cases, has been the continuous military and humanitarian support offered to the Ukrainian government.
In some cases, the goal is to delay the help, which is a win in its own rights. NoName has been active in the cybercriminal space since 2022, shortly after Russia invaded Ukraine. The hackers were transparent with their affiliations and goals from the beginning.
According to their initial post, they were hell-bent on sabotaging Ukraine’s ability to resist the Russian will. Along with the will of its allies to keep funding Ukraine’s war efforts.
How to Protect Yourself from NoName?
The harsh reality of things is that there is little you can do to keep NoName away. If they consider you a target of interest, all you can hope for is ways to mitigate the fallout. NoName’s attacks aren’t generally extremely debilitating, which is the good news.
It’s important to note, however, that NoName primarily targets governmental institutions. That’s because these are the most influential in the ongoing war efforts and deserve their special attention. But that’s not always the case.
The hackers can also target private companies if they feel like they make a noticeable impact on their radar.
Just to preempt it, NoName is known to conduct a variety of operations with a multitude of tactics. They use DDoS floods as standard attack MOs, but that’s not their entire arsenal.
The hackers also use disinformation, propaganda, character assassinations, threats, and blackmail, among other things, to achieve their goals. This makes it very difficult to preempt and prepare for NoName, as you never truly know what to expect.
Which is to say that the war between cybercriminal gangs like NoName and the rest of the world will continue as usual for the foreseeable future.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

