Pro-Russian NoName Targets Spain
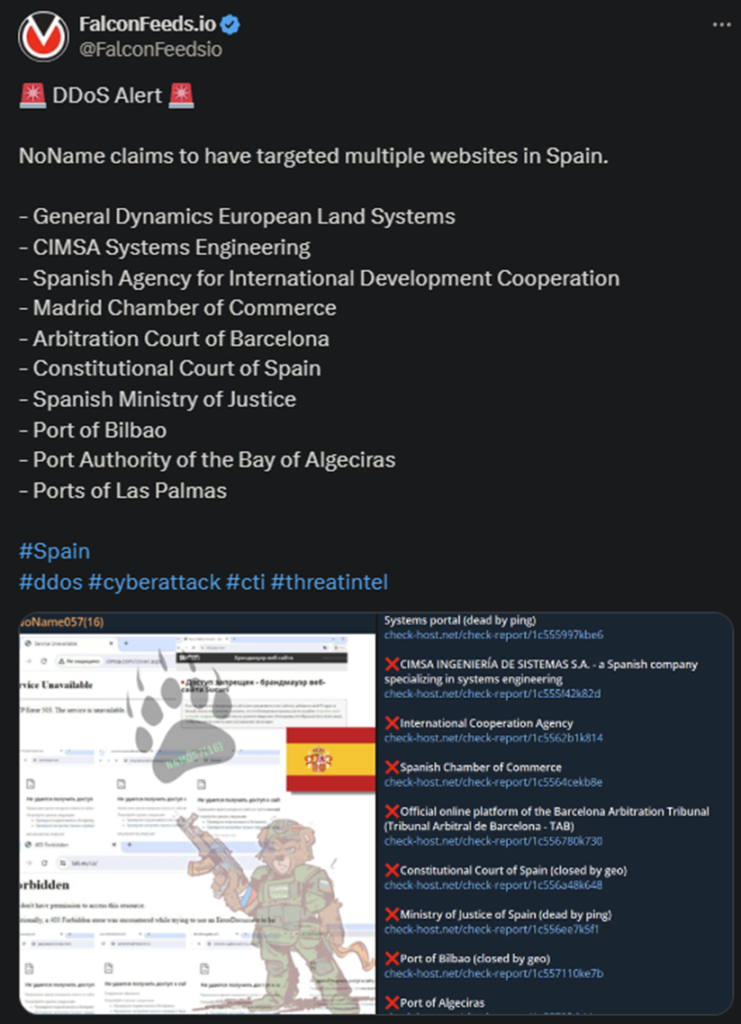
NoName announced a new operation, this time against Spain. The attack targeted multiple websites, including those of the Constitutional Court of Spain and the Madrid Chamber of Commerce. This is the latest of a string of attacks against the Spanish government.
- In total, NoName’s attack targeted 10 Spanish websites, all being public institutions
- The NoName hackers prioritize state-owned to send a message and impact the government’s ability to run its business
- NoName’s attacks are almost exclusively politically-motivated
- The infamous cybercriminal organization holds entrenched pro-Russian views, and its self-stated goal is to protect the Russian state
The Spanish government hasn’t commented on the situation yet, but NoName has hit the Spanish news before. The hackers have been conducting DDoS operations against Spain and numerous other countries since the beginning of the Ruso-Ukrainian war.
The pro-Russian cybercriminal organization aims to target all anti-Russian nations, prioritizing those who actively support the Kyiv regime. Spain is one of them. Pedro Sanchez’s government has displayed pro-Ukrainian views over the past 2 years.
The recent political agreement signed between Sanchez and Zelenski in May at the Moncloa Palace strengthened that commitment.
The meeting laid out a 10-year support plan between Spain and Ukraine, with the former aiming to deliver increased military and humanitarian aid moving forward. 2024 is already looking at a 1-billion-euro package for Ukraine, consisting of military aid.
Part of that comes in the form of anti-air defense, which Ukraine sorely needs. And that’s not all. The Spanish government will also provide 15 million euros to Ukraine and Moldova for recovery purposes, along with other multiple millions for humanitarian purposes.
What’s NoName’s Goal?
NoName is a strict pro-Russian entity with vested interests in protecting Russia’s reputation and goals. To that end, the hackers conduct at least one hit per day, usually more. In most cases, NoName produces multiple victims daily, as is the case with today’s attack.
The typical victimology includes anti-Russian states that support the Ukrainian government directly. This is either via military or humanitarian means or both. The hackers will prioritize those who have already sent aid packages to Ukraine or plan to.
Next in line come those who merely state their support but without necessarily contributing. This means that NoName can attack both public and private institutions, depending on their involvement in the matter.
The cybercriminal organization relies on DDoS attacks to send their message. These are typically non-intrusive operations, relying on bot floods to overwhelm the target website with access requests. The attack usually takes the website down.
In most cases, the victim’s services are back online shortly after, but not always; sometimes, it may take days or even weeks. Which is to say that even DDoS attacks can cause significant structural and financial damages.
So far, it isn’t clear whether NoName’s attacks have had any meaningful impact on the public conscience. Governments are aware of the perpetrator and its goals and deal with the aftermath of an attack relatively quickly.
But there’s no evidence that the attacks have swayed the victim from contributing to the ongoing war. Not for now, at least.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

