Australian Online Store Database Allegedly Leaked by Hackers
A hacker alleges to have acquired the entire database of an Australian online store, potentially impacting tens of thousands of customers. The authenticity of the leak has yet to be confirmed.
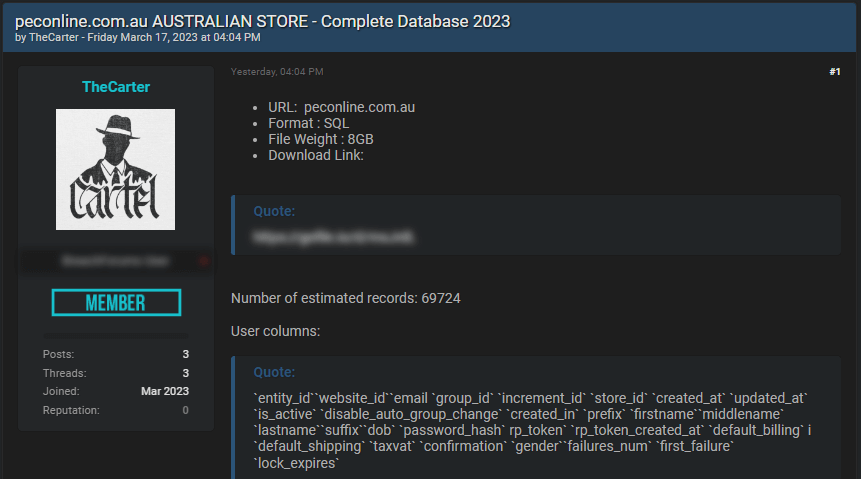
- Hacker asserts possession of a database from the Australian online store, http://peconline.com.au
- Purported data consists of email, name, gender, and password, impacting approximately 69,724 records
- Potential consequences for users encompass identity theft, phishing, and various cybercrimes
- Users are advised to implement measures to strengthen their online security
A participant on a hacker’s forum contends that they have procured a comprehensive database from an Australian online store, http://peconline.com.au. The claimed data encompasses sensitive details such as email, name, gender, and password, possibly affecting around 69,724 customers.
Should the leak prove genuine, users may be vulnerable to identity theft, phishing schemes, and other types of cybercrime.
The alleged data leak was announced on a popular cybercrime-related forum, where the user claimed to possess the entire database of the Australian online store.
It is unclear at this moment how the database was obtained or the time of the alleged data breach.
Authenticity of the leak cannot be determined
Samples of the alleged data were provided by the hacker, but the authenticity of the information cannot be determined.
The forum post was created by a user who has been involved in confirmed data breaches and the sale of illegally obtained databases in the past.
Implications for users
If the data leak is authentic, affected users could face various cybersecurity risks. The stolen information could be used for identity theft, phishing attacks, or even to access other online accounts if users have reused the same password.
In addition, cybercriminals could impersonate victims and attempt to extort money from them or their contacts.
What users can do to enhance their security online
Given the potential risks associated with the alleged data leak, users are urged to take the following precautions to enhance their online security:
Update passwords: It is recommended that users update their passwords for any accounts connected to the online store and refrain from using identical passwords for multiple accounts.
Implement two-factor authentication: Users are advised to activate two-factor authentication on their accounts when available, providing an additional security barrier.
Beware of phishing schemes: Users must exercise caution when dealing with unexpected emails or messages, even if they seem to originate from a trustworthy source. Confirm the legitimacy of the sender prior to clicking on links or downloading any attachments.
Keep track of account activities: Users are encouraged to routinely check their online accounts for unusual activities and promptly report any suspicions to the relevant platform or service provider.
Stay up-to-date on data breach news: Users should remain aware of data breach incidents and take necessary steps if their personal information is implicated in a breach.
While it remains undetermined if the alleged data leak is authentic, users should always take necessary precautions to protect their online security and minimize potential risks.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

