Cyber Dragon Attacks And Disables Linkedin
The lesser-known but dangerous hacking group Cyber Dragon took Linkedin offline recently as a result of a massive breach. As users reported, both the website and the app were down for more than 24 hours intermittently.
- Cyber Dragon is a peculiar hacking actor with both Chinese and Russian ties
- LinkedIn didn’t comment on the event, but the forums were filled with people complaining about the problem
- Cyber Dragon posted evidence of the attack on their TOR platform, but the real reason behind the breach is unclear
- LinkedIn has been the victim of cyber-attacks numerous times in the past
Many of the attacks against LinkedIn have resulted in massive data leaks. A February 2023 breach led to more than 500 million user accounts being exposed by the hackers. These were then put up for sale on the dark web.
The sale was auctioned by the hackers with a starting price of $1 million. Only 3 days later, the hackers posted another 327 million accounts on sale for $7,000 bitcoins. This wasn’t the only such event, as LinkedIn has been breached several times during 2023.
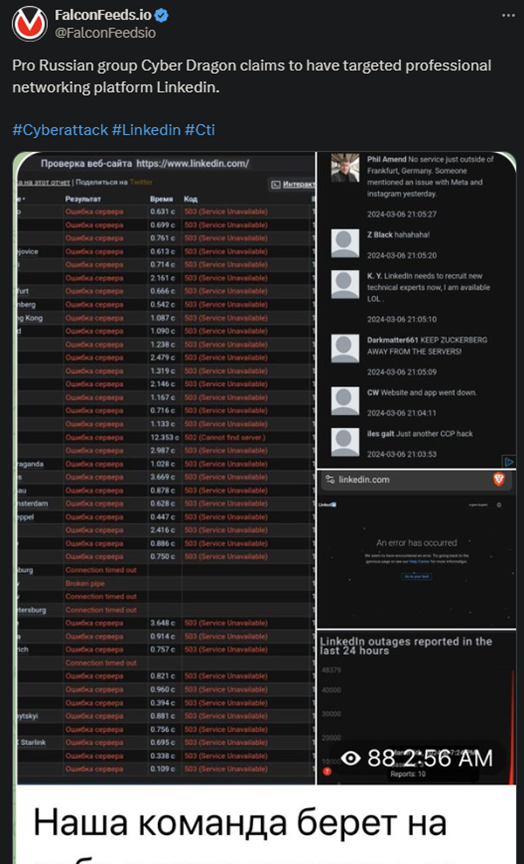
However, it appears as if the hackers didn’t make any special requests this time around. It’s unclear if the event resulted in any data leak or whether this was a DDoS attack meant to disrupt the platform’s services.
That being said, ransomware groups don’t always negotiate with the victims. Most ransomware organizations rely on the double extortion practice, encrypting the victim’s files and stealing sensitive data.
They will then negotiate for both the decryption key and the deletion of the data, which can result in juicy financial gains if the victim decides to pay. However, not all ransomware actors use this approach.
Others will simply breach their victims, steal data, and sell it directly on the dark web. This is more likely to happen in the case of breaching social platforms like Meta, Reddit, Twitter, Linkedin, and others.
Who Is Cyber Dragon?
The infamous hacker group is known to have pro-Russian ties, both from the organization’s own statements and because they post mainly in Russian. They are also known to often choreograph cyber-attacks with other pro-Russian organizations.
However, some connections have been found between Cyber Dragon and Chinese hacking entities. This wouldn’t be extraordinary, given that Russia and China are allies on the global stage.
But it’s the Russian shade that holds the most weight and influences the group’s action. This suggests the idea that Cyber Dragon may be choosing some of its targets based on their ideological and political affiliations. This isn’t new in the cybercriminal sphere.
NoName is another such group with powerful Russian ties that pushes pro-Russian narratives and propaganda. However, the situation isn’t as clear with Cyber Dragon as it is with NoName.
Based on the organization’s history, it does appear to prioritize financial gains above all else. Despite not promoting itself as a ransomware entity, Cyber Dragon most likely operates like one based on the available evidence.
They haven’t made any request in this sense, so this theory is yet to be confirmed.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

