Inc Ransom Targets 3
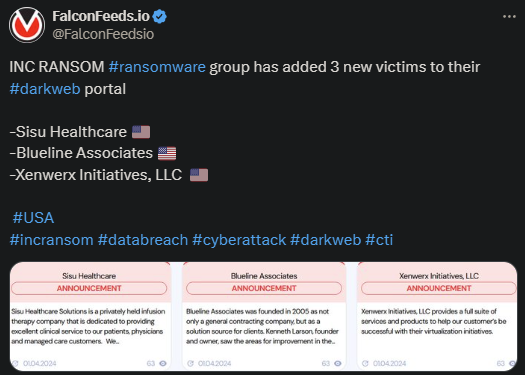
Infamous Inc Ransom targets and breaches 3 US-based companies. These are Sisu Healthcare, Blueline Associates, and Xenwerx Initiatives, LLC.
- Inc Ransom is a controversial ransomware actor, as some people suggest it only exists as a name, not as an actual cybercriminal group
- Inc Ransom was first observed publicly in August of 2023, which makes it a new organization
- The Inc Ransom hackers have proven to be extremely inventive, resourceful, an difficult to negotiate with
- Neither of the 3 victims has come forth with a public statement regarding the ransomware incidents
Despite being new on the market, Inc Ransom has grown fast and gained a reputation as a fearsome gang. They consistently target medium and high-value targets and show extreme effectiveness during and after the breach.
Inc Ransom hackers are notorious for their unique approach to the ransomware business. Rather than advertising themselves as what they are: cybercriminals, they instead self-qualify themselves as service providers.
The hackers state that their goal is to breach various targets and expose their system vulnerabilities. The ransom that the victim is then forced to pay represents the fair payment for the hackers’ services.
Many have pointed out that this type of reframing is non-sensical because it’s indistinguishable from standard ransomware practices. Calling it something else doesn’t mean it is something else.
Ransomware breaches have increased slightly during 2023, compared to 2022, and it’s unclear why. 2023 also saw the rise of several ransomware actors, Inc Ransom being one of them.
That being said, the same year marked visible advances in the war against ransomware organizations, as the FBI has conducted several operations in this sense. The latest one is the Cronos operation, whose goal was to destroy Lockbit.
What or Who Is Inc Ransom?
The shortest and straight-to-the-point answer would be that Inc Ransom is a standard ransomware group. But that wouldn’t paint the whole picture. In reality, Inc Ransom is a very shady ransomware gang that many argue doesn’t even exist.
One of the pillars supporting this theory is the fact that Inc Ransom shows code and tactic similarities with several other ransomware gangs. One of them is Lockbit. What does this mean?
It means that there’s a possibility that Inc Ransom is actually a cardboard ransomware actor. A façade that legitimate ransomware organizations use as a suit to cover their tracks and take some heat off their trails.
This isn’t confirmed, but it’s not a preposterous theory, as it wouldn’t be the first time this has been observed. Inc Ransom hackers deny such theories, which isn’t surprising.
When it comes to its MO, Inc Ransom follows the standard double-extortion practice. The hackers will infiltrate the system, cover their tracks, encrypt the victim’s files, and extract valuable data for ransom.
The victim will then have to negotiate for both the decryption key, as well as the deletion of the stolen data. Experts warn that paying the ransom doesn’t guarantee anything, except for, in the best-case scenario, the decryption key.
But just because you pay for the hackers to delete the data doesn’t mean that they will. This is why professionals advise against any type of negotiation with ransomware hackers.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

