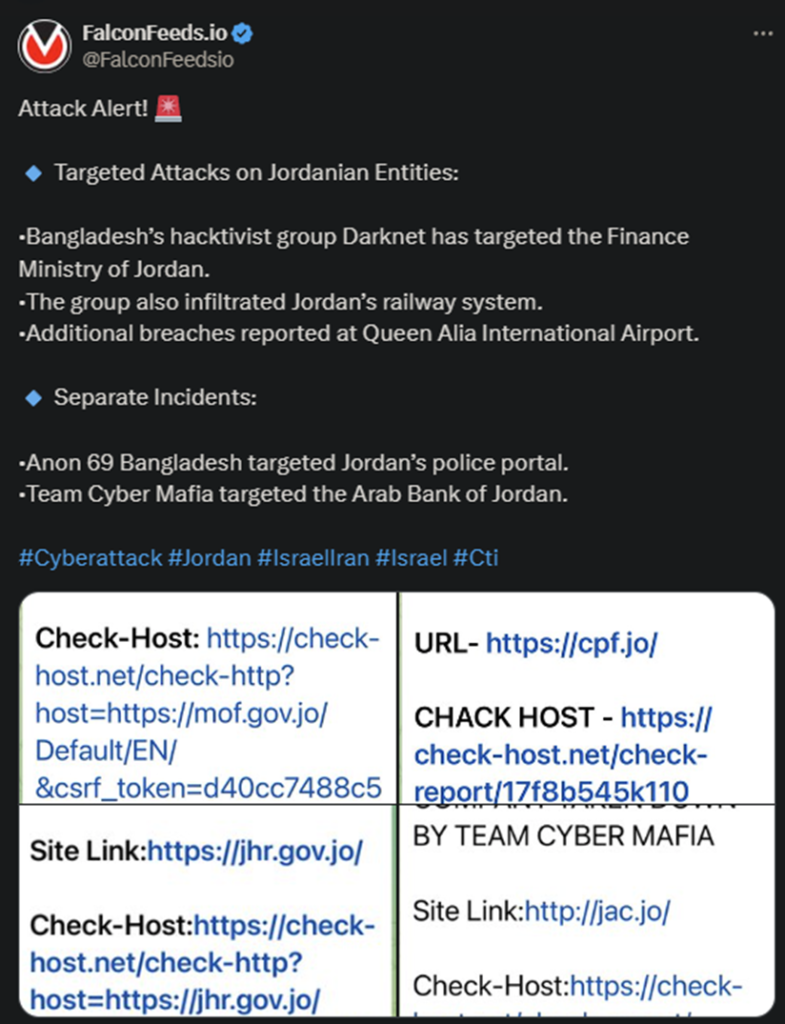
Jordan is Under Attack
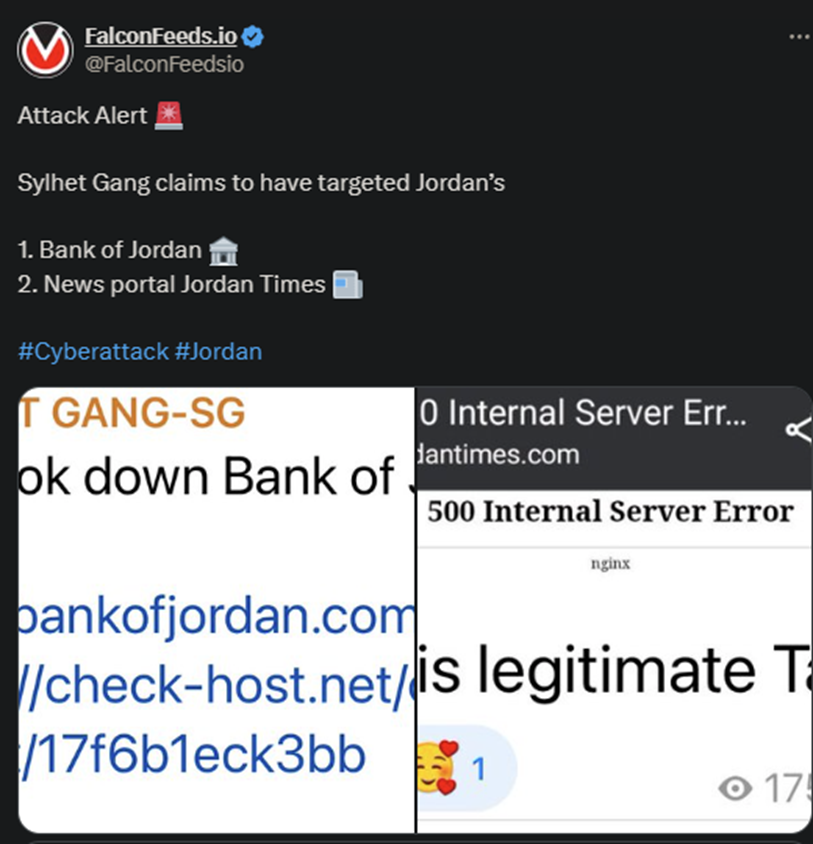
Several Jordanian targets have been hit by four different hacktivist organizations, Darknet, Sylhet Gang, Anon 69 Bangladesh, and Team Cyber Mafia. Some of the targets being hit include Jordan’s Finance Ministry, its railway system, the Bank of Jordan, and the news portal Jordan Times.
- The hackers haven’t explicitly stated a clear reason for the attack, but one can be easily deduced
- Jordan is siding with Israel in its ongoing war against Hamas as well as against any other type of foreign threat
- According to the latest information, Jordan also intercepted some of the drones fired by Iran at Israel’s Iron Dome recently
- Cyberattacks were to be expected in the context of the escalating tensions between Israel and some of its neighbors
Darknet and Sylhet Gang are very poorly covered in the public sector, as they seemingly rank low on the threat scale. This may change soon, given the impact of their recent operations against Jordan’s infrastructure.
One of the few things we know about them is the fact that they’re of Indian descent. Darknet is Bangladesh’s unofficial hacktivist group while Sylhet Gang also shows Indian ties. This may sound bizarre, given that India has recently expressed support for the Israeli cause.
And if that’s not enough reason for confusion, let’s consider a third operation conducted by Sylhet Gang against Israel itself, which took place at the same time. This means it’s safe to say that these attacks may not necessarily reflect any government’s will and intentions.
Instead, they may be the work of rogue organizations with a personal interest in the intrusions. It’s unclear if any data has been stolen, and the hackers haven’t made any political or ideological statements following the attacks.
So, the real reasons behind the attacks remain unknown.
Is There a Connection Between the Attacks?
There’s no clear evidence that there is, but the current context does support the theory that there is one. Cyberattacks have been the bread and butter of any respectable war actor and the ongoing Russia-Ukraine conflict is proof of that.
Both sides attack, spy, and infiltrate each other in hopes of gaining the upper hand in the information war. Or, better yet, impact the other party’s ability to continue to resist.
In doing so, war actors often rely on third-party cybercriminal groups and even rogue affiliates to conduct these operations. This allows them to perform attacks with plausible deniability since there are no leads pointing at them.
Is that the case with these recent attacks? It’s unclear for now since no theory has been definitively confirmed. It’s important to note that the notion of cyberwarfare doesn’t resume strictly to cyberattacks.
It may also involve stealing data, stealing the victim’s identity, practicing extortion and blackmail, sending threatening letters or emails, doing character assassinations, and so on. Propaganda, misinformation, and attempts at defamation are also used to great effect.
These recent attacks raise concern about the rise in cyber breaches made with political or ideological goals. They also sound the alarm regarding the emergence of increasingly more cybercriminal gangs willing to make a name for themselves.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

