LockBit Produces Mass Casualties
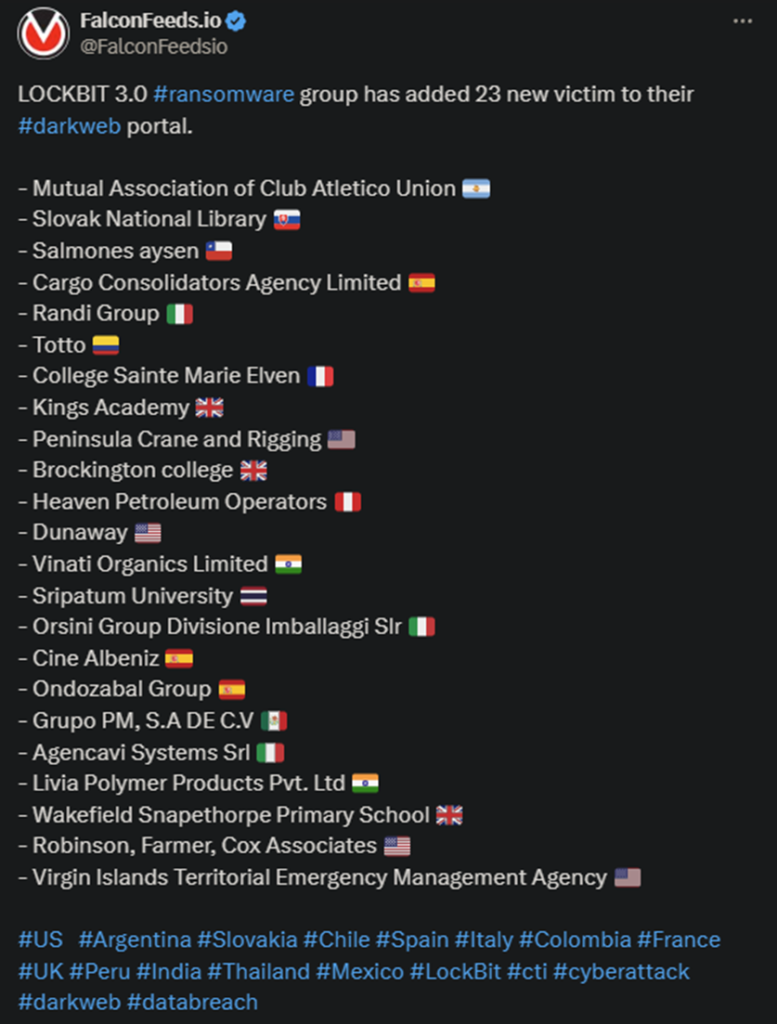
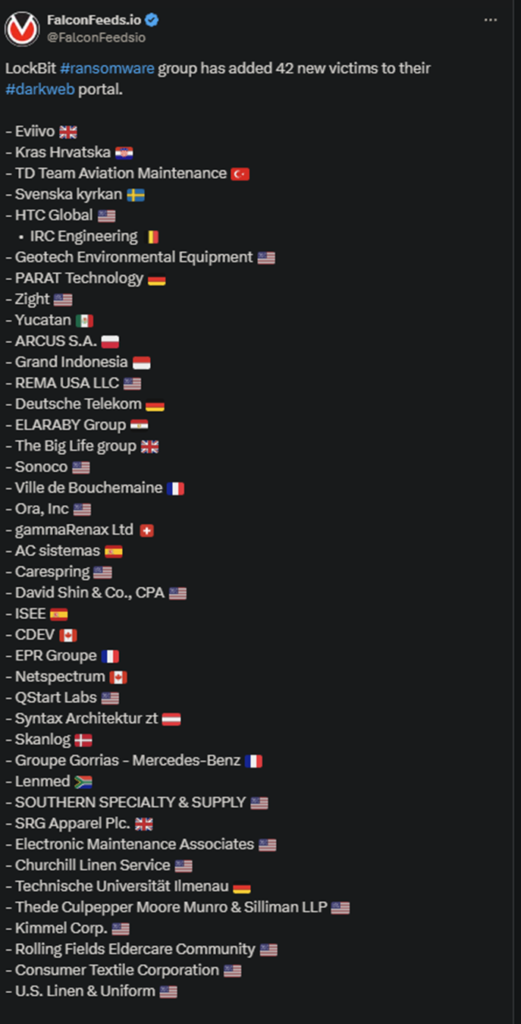
LockBit announced a massive ransomware operation that targeted 23 victims recently. This hit comes days after an even larger one on the 7th, during which the hackers infiltrated 42 targets. The victims are spread out across multiple countries.
- Some of the countries targeted by LockBit include Argentina, the US, the UK, Peru, Spain, Chile, France, and Italy
- The victims are all medium and high-value targets with considerable revenue values
- The most prominent victims include the UK’s Kings Academy and Brockington College, the Sripatum University from Thailand, and the Italian Randi Group
- LockBit operators haven’t published any other details about the operation aside from brief summaries of each victim
This is one of the largest ransomware operations to date, following the one several days ago when the hackers targeted 42 institutions. The scale of the attacks is unusual even for LockBit, despite its reputation as the fiercest ransomware actor in the world.
Some suggest that these recent operations are proof of LockBit upgrading its systems and tactics. This allows the organization to operate at a higher magnitude, targeting multiple businesses over shorter periods of time.
It’s also impressive that the hackers have managed to identify and breach so many vulnerable victims. Especially given that most ransomware attacks fail to achieve their goal.
It’s unclear at this point whether the victims have decided to negotiate with the LockBit operators. The hackers also haven’t posted any information regarding the value of the ransoms or how much data they’ve managed to steal.
LockBit is the largest and most advanced ransomware organization in the world. According to the FBI, the organization is not only the most successful in terms of results, but the most well-funded as well.
Operation Cronos, which aimed to destroy LockBit back in February of the current year, revealed that the group had over $112 million in ransom gains up to that point. It is presumed that these numbers have gone up since then.
How to Prevent LockBit Attacks?
This is undoubtedly a burning question, given LockBit’s latest rampage. The answer is fairly simple, but complex too at the same time. LockBit generally resorts to typical MOs like spear-phishing to gain access to the victim’s system.
In some cases, they may use stolen credentials acquired from third-parties or even infect legitimate software. Some of these methods can be prevented, while others not so much.
There’s nothing you can do if the hackers steal your credentials from a legitimate platform as a result of an internal data leak. Prevention can do a lot to mitigate some of the risks associated with ransomware breaches, but not all.
This means that you need to have a plan B in place for when you actually get breached. Which, if you’re a medium-to-high-value business, will happen at some point. In that case, experts recommend a no-negotiation approach.
Create backups for the data and avoid contacting or negotiating with the hackers. Or, worse, pay the ransom. All that does is to mark you for future breaches because the hackers always return to those who pay.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

