Massive Ransomware Leak at India’s CredRight
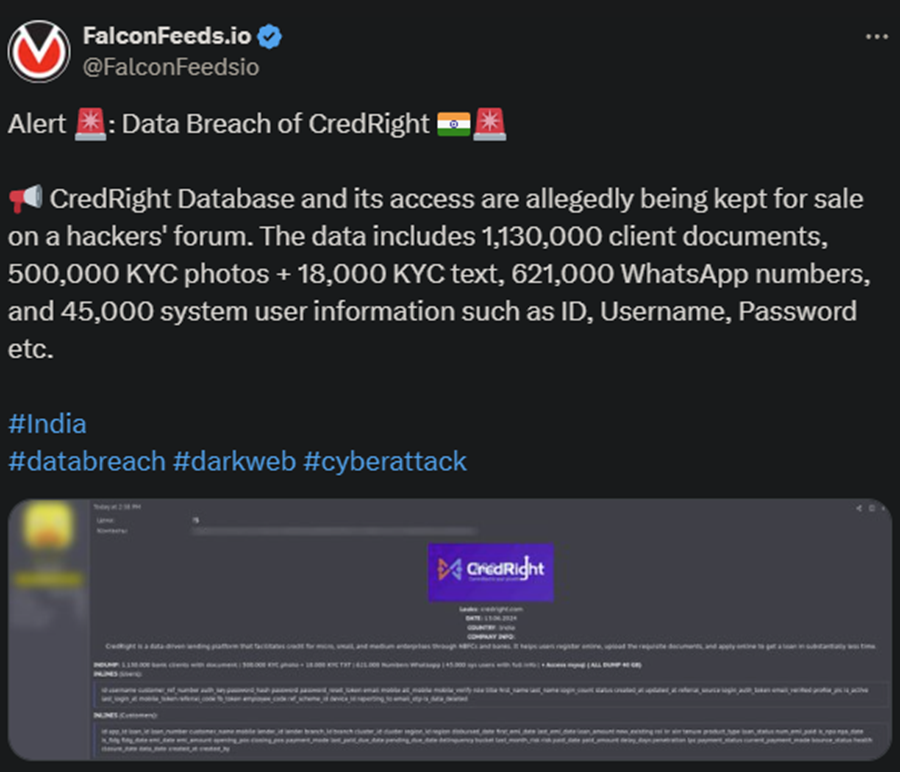
An unknown hacker posted a massive database of information belonging to India’s CredRight. CredRight is a lending platform that connects micro, small, and medium companies to NBFCs and banks. CredRight hasn’t confirmed the breach.
- The hackers haven’t disclosed their identity, so it’s unclear if this was the work of a legitimate ransomware gang or a rogue cybercriminal operator
- The data leak is supposedly massive, involving 40 GB of highly sensitive information
- The attack was marked as a ransomware hit, but it’s unclear if that’s the case, given that there’s no evidence of any demands or negotiations
- Another theory is that the hackers skipped the entire negotiation process and started selling the data immediately
In most ransomware attacks, the hackers will leave a ransomware note behind and demand payment to delete the stolen data. They will always attempt to get money from the victim first and only sell the data as a last resort.
That’s because the victim is the most interested in the data. If negotiations fail or the target company simply refuses to contact the hackers, only then will they market the stolen data. It’s unclear whether CredRight’s situation falls in the former or the latter category.
It’s important to note that the data leak contained a lot of customer information, which is already a massive problem for CredRight. Ransomware attacks, or any other cyberbreaches that result in considerable data leaks, are always a reason for concern.
That’s true for both the company being breached and the victims who are directly impacted by the data leak. The company can be held liable for any data leak that may result from poor cyber defences.
This is why many victims refuse to acknowledge or report the breaches. It’s unclear if this is the case with CredRight, and it hasn’t been confirmed whether the attack actually took place.
But, from the initial reports, the breach seems to be legit.
Who Attacked CredRight?
Realistically speaking, it could be anyone. Most likely, though, it’s a legitimate ransomware entity. One that values privacy and money more than fame. This would explain why nobody has claimed the attack openly.
This usually happens with ransomware gangs that have been targeted by law enforcement agencies. Delivering anonymous hits allows them to continue their operations without attracting even more heat from CISA, FBI, or Interpol.
It’s important to note that, despite remaining publicly anonymous, the hackers may reveal their identities to the victims. Especially if the data being stolen is of high value. That’s because the hackers can negotiate with the victim behind the scenes.
The victim doesn’t want to report the breach to the local authorities, while the hackers don’t want their identity exposed publicly. So, they agree to settle the matter behind the curtains. This usually consists of the ransom being paid far from the public’s eye.
This doesn’t appear to be the case with the CredRight situation, as the hackers have leaked the identity of the victim. So, they’re either not interested in any agreement, or negotiations have failed, so now they’re making the most of a failed situation.
Whatever the case may be, the situation is still developing.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

