Medusa Ransomware Attacks Brazil
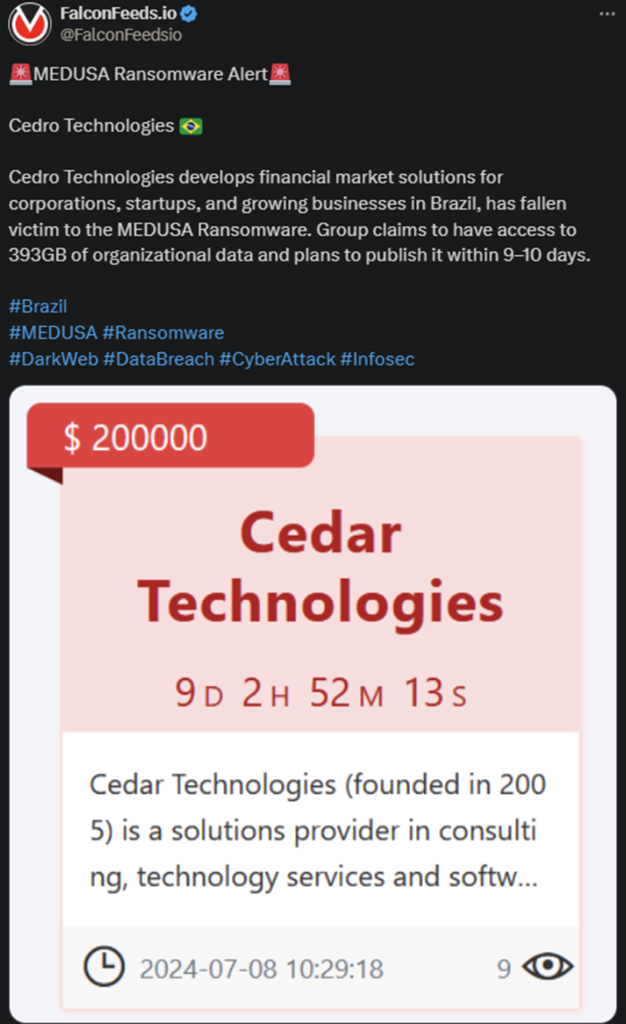
Medusa hackers announced another breach recently, this time taking place in Brazil. The victim is Cedro Technologies, a financial solution provider for corporations and growing businesses. The companies’ representatives haven’t commented on the situation.
- According to Medusa’s original announcement post, the attackers managed to leak around 393 GB of sensitive data
- As stated in the same post, the victim has 9 days remaining to contact the hackers for negotiations
- A price tag of $200,000 is also visible, hinting at the value of the ransom, albeit unlikely
- Medusa also offers several price options, depending on the victim’s goals
While Medusa isn’t necessarily that much different from your typical ransomware gang, they do things a bit differently. As a RaaS (Ransomware-as-a-Service), the organization relies on affiliates to conduct most of its operations.
This decreases the financial investment and allows the gang to cover their tracks more easily. This is typical MO for RaaS-based organizations. So, what does Medusa do differently?
One thing that makes Medusa stand out is its flexibility. Most ransomware gangs are very blunt with their negotiations. The ransom is what it is, and you either take it or leave it. Some will negotiate the value of the ransom, but only marginally.
However, Medusa offers its victims several payment options. The victims can pay for extension days until the data leaks publicly, pay to download the data and pay to require the deletion of the data. The latter is part of the ransom payment.
Naturally, the sums to pay for the different services are predictably steep, usually revolving around tens or hundreds of thousands of dollars. The prices vary based on the victim’s profile and projected revenue.
How to Deal with Medusa?
It’s clear that Medusa is a veteran in the ransomware space. The organization first hit the public sphere in Q4 of 2022 but started attracting attention in Q1 of 2023. Since then, Medusa has been linked to a variety of hits across the Globe.
The hackers prioritize the technological market but also target education, manufacturing, healthcare, wholesale, and legal services. The goal is always financial in nature, as is typically the case with ransomware attacks.
So, what should you do if you’re targeted by Medusa? There are several things to consider. The first is to confirm that this is the actual Medusa gang rather than MedusaLocker. The 2 are unrelated but bear similar names.
Then you should alert the authorities regarding the breach, despite what the hackers are telling you. This helps law enforcement keep track of the gang’s activity, which will help with the subsequent operations. Then you should ponder over the ideal solution to your problem.
The problem is that your files are encrypted, and the hackers have your sensitive data. The standard recommendation is to avoid any contact with the hackers and work with professionals to decrypt your system and recover the data.
You should also not pay the ransom because that will most likely mark you as a target “worthy of revisiting.” And nobody wants that, aside from the hackers.
That being said, you should always prioritize prevention above all else. It’s always preferable to prevent the breach than deal with it after it has occurred.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

