MEDUSA Ransomware Entangles 2 New Victims
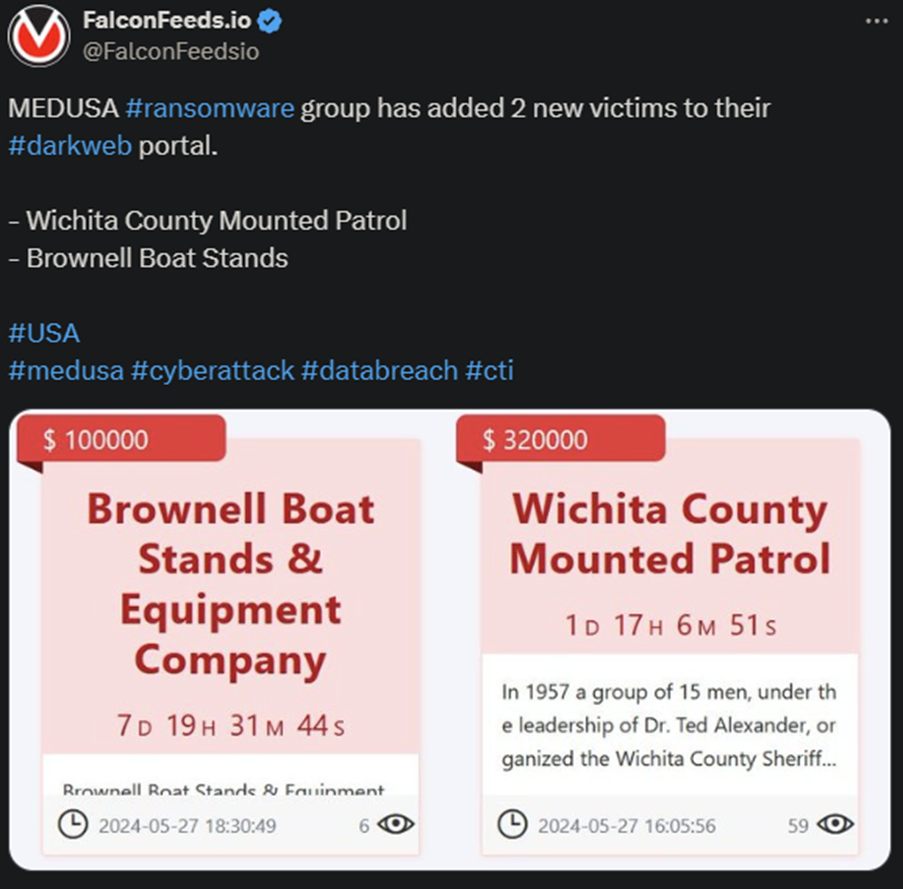
The infamous MEDUSA ransomware gang announced 2 new victims on their leak blog. These are US-based Wichita County Mounted Patrol and Brownell Boat Stands, the former being active since 1957.
- The hackers posted the news about the breaches on their trademark Medusa Blog, along with short summaries for each victim
- The attackers also gave the victims several payment options, as they usually do
- According to the original post, one victim has little over 7 days left to contact the hackers, while the other has just under 2 days remaining
- MEDUSA has been ramping up its activity visibly since early 2023, which coincides with the public release of their Medusa Blog
MEDUSA has been at the forefront of cybercrime throughout 2023, carrying out multiple ransomware operations since the beginning of the year. The gang appears to be more versatile, inventive, and resourceful than your typical ransomware organization.
While most ransomware gangs rely on the tried-and-tested spear-phishing to gain access to the clients’ systems, MEDUSA takes on a different approach. The hackers prefer to infect vulnerable public services and platforms as primary MO.
This gives the hackers access to an extensive database of unsuspecting clients who are completely oblivious to the danger. They also hack high-profile accounts directly, which typically gives the hackers access to their business credentials.
This approach boosts MEDUSA’s success rates dramatically but also carries more risks. Hacking into a legitimate platform or app is bound to leave breadcrumbs behind. Fortunately for them, the hackers are extremely cautious, always wiping any trace of their intrusion.
Once in, MEDUSA operators will employ the standard MO, encrypting the victim’s system, exfiltrating valuable data, and manipulating the system to evade detection. The gang is extremely competent and resourceful, which explains its high success rate.
What to Know About MEDUSA?
It’s important to note that, despite being another ransomware actor, MEDUSA isn’t just any ransomware actor. The organization has some rather atypical approaches to the business. One important one comes in the form of the payment options they offer.
Most ransomware gangs have the ransom itself as the only requirement. But MEDUSA is more versatile than that. The hackers provide the victim with several payment options, as follows:
- The standard fee for data extension, in case the victim needs more time to ponder over the situation ($10,000 per additional day)
- A fee for data downloading
- A fee for requesting the operators to delete the stolen data
The latter 2 don’t have a fixed amount. Instead, the value of the fees varies based on the victim’s overall revenue. The largest fee is understandably the last one, asking for data deletion. That would be the ransom itself.
A crucial point here: the fees that the victim ends up paying may not be 1:1 with the amounts already on display. It all depends on how the negotiations unfold.
MEDUSA also works as a RaaS (Ransomware-as-a-Service), relying on affiliates to boost their profits with minimal efforts and investments. It’s a successful business model, if we look at MEDUSA’s activity level and attack frequency.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

