Medusa Ransomware Stunlocks 2
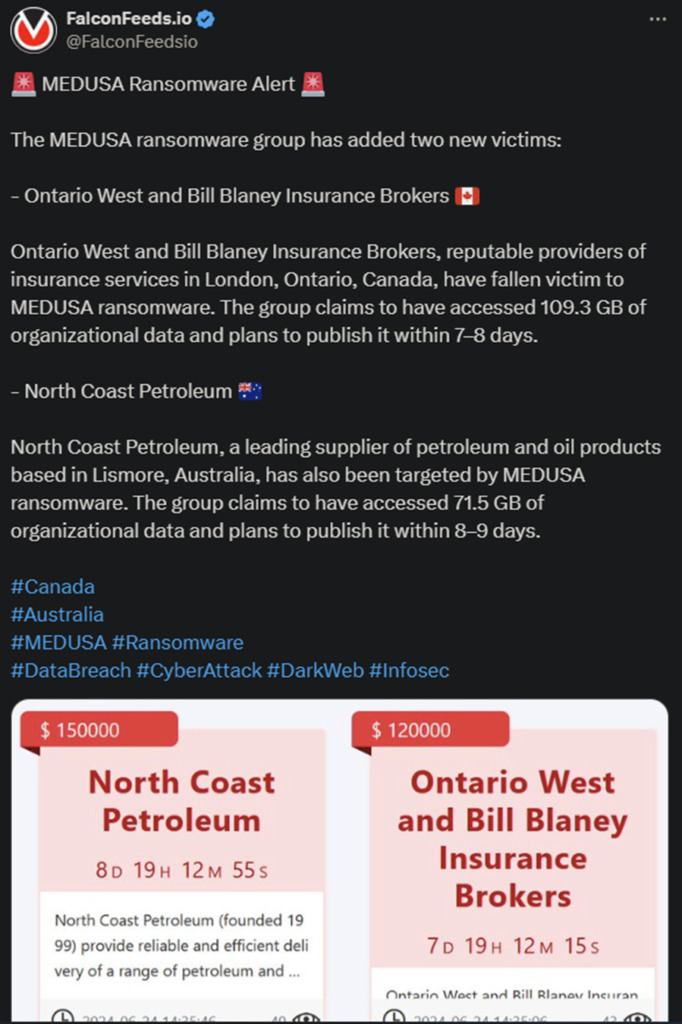
MEDUSA has announced 2 more victims recently. These are Canadian-based Ontario West and Bill Blaney Insurance Brokers and North Coast Petroleum from Australia. The hackers allegedly stole between 71.5 GB and 109.3 GB of sensitive data.
- MEDUSA relies on the double extortion technique to increase its leverage during negotiations
- Aside from employing a powerful encryptor, the hackers also steal confidential data, which they threaten to leak online unless the ransom is paid
- According to the hackers’ original post, the victims have up to 8 days at their disposal to pay the ransom
- None of the company representatives have commented on the situation unfolding
MEDUSA operates as an RaaS, so it relies on affiliates to conduct most of its operations. The affiliates get to keep most of the ransom (typically between 70% and 90%, depending on the case) with the rest going to the owners themselves.
This business model is highly lucrative for MEDUSA, as the actors get paid royally while investing and risking almost nothing. According to the latest reports, MEDUSA is responsible for close to 200 successful hits since February, 2022.
This ranks it as the 8th most prolific ransomware gang in the world.
Unlike other ransomware actors, MEDUSA likes to provide the victims with several payment options. The hackers appear to me a lot more malleable in this sense. Following a successful breach, the victims can:
- Pay for payment extension (X amount per day)
- Pay to download the data
- Pay to request the deletion of the data
The dollar values attributed to each point vary depending on the victim’s profile and revenue. In addition to that, MEDUSA also displays the ransom in their announcement post. In this particular case, the victims are required to pay $120,000 and $150,000 respectively.
These values can change during negotiations, depending on how the talks go.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

