NoName Attacks Finland and France
NoName posted another announcement, this time throwing Finland and France into the fire. The hackers mocked the two governments after breaching their cyber defenses and bringing their websites down.
- The hackers justified the attack by pointing at Finland’s and France’s support for the Ukrainian government
- NoName has become known in the cybercriminal space as one of the most active pro-Russian cybercriminal gangs in the world
- None of the two countries’ representatives have commented on the situation
- The websites were still down at the writing of this article, but it is presumed that they’ve been restored since
NoName’s true identity is still unknown, which is rather impressive given the organization’s aggressive activity level and longevity. The gang first came public at the end of February 2022, when Russia first invaded Ukraine.
The hackers immediately pledged allegiance to the Russian government, stating that they would attack anyone who opposed its will. Naturally, Ukraine was at the top of the list, but its allies followed suit quickly.
NoName has conducted numerous attacks across the globe, primarily targeting those who have supported the Kyiv regime directly. Some of the victims include the US, Germany, Moldova, Poland, Finland, France, Romania, the Czech Republic, and Canada.
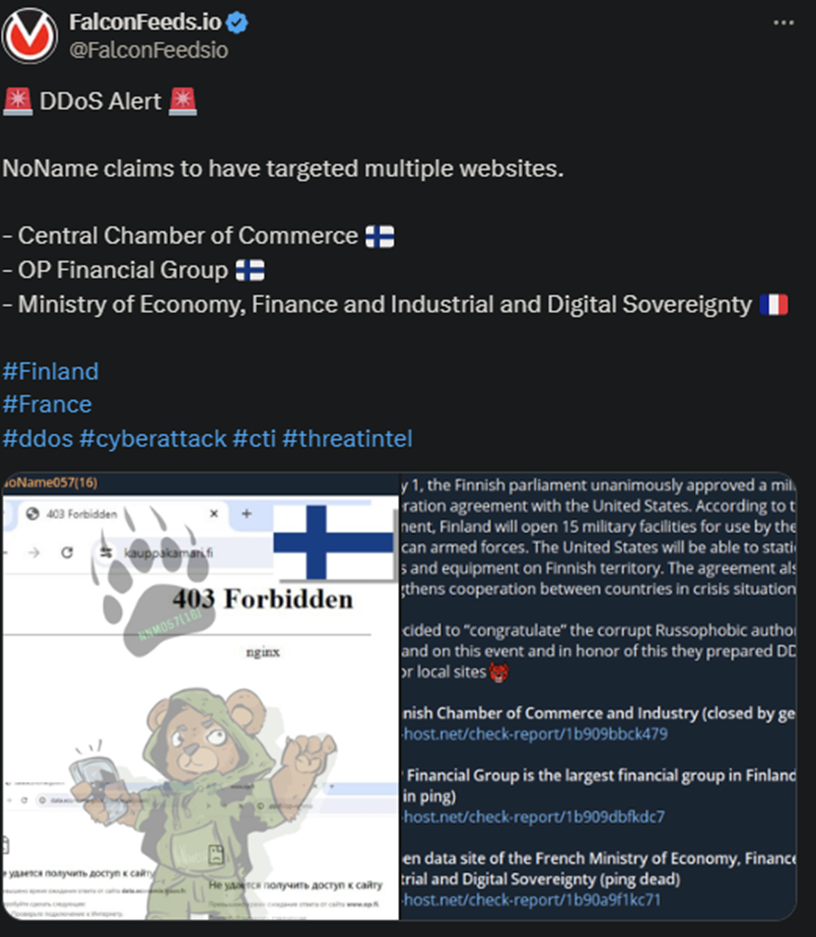
Today’s attacks have been motivated by Finland’s decision to allow the US to use 15 military facilities on its territory. This has been seen as an aggressive move by Putin, which condemned the US’s and NATO’s spread over the past several years.
NoName reacted immediately, targeting the Central Chamber of Commerce and the OP Financial Group in Finland and the Ministry of Economy, Finance, and Industrial and Digital Sovereignty in France.
What Does NoName Want?
NoName’s sole purpose of existence is the continuation of the Russian state. At least according to their self-stated goals. To this end, the hackers employ a variety of strategies, with DDoS attacks being the primary MO.
Other non-conventional tactics include threats, public mocking, blackmail, data leaks, propaganda, spreading misinformation, and even sending real-life threats to their victims. NoName also attacks a variety of institutions, regardless of their scope or size.
Naturally, the hackers prioritize state-owned institutions, especially those that manage public services. These include the public sector, emergency services, healthcare, public transportation, and others. The gang also targets private companies in some cases.
In the case of the latter, the trigger remains the same: the direct or indirect support shown to the Ukrainian government. In some cases, the targets have either delivered or are in the process of delivering military or humanitarian aid. In others, they’ve promised to do so.
When it comes to the standard MO, NoName relies almost exclusively on DDoS attacks, especially over the last year. These types of attacks involve sending millions of bot requests to the target website.
The sheer volume of requests causes the website to crash, sometimes with long-term consequences. The attacks aren’t particularly devastating, but they’re not meant to be. The goal is to send a message and intimidate the victims.
So far, NoName’s attacks didn’t have a meaningful impact, aside from the temporary effects on the victims’ cyber-structure.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

