NoName Continues Its Ukrainian Crusade
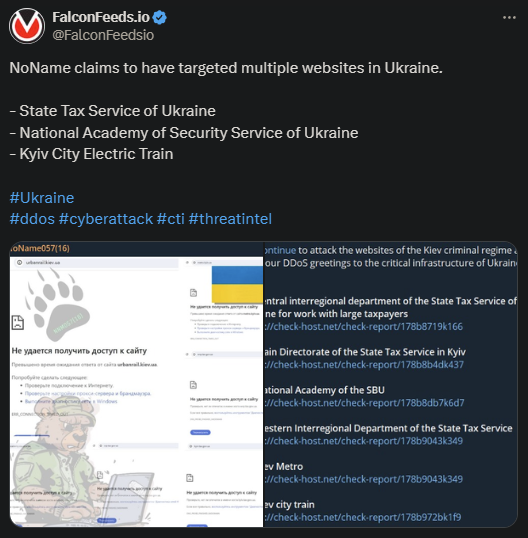
NoName announced yet another hit on Ukrainian websites, this time targeting 6. These are public institutions like Kyiv City Electric Train, the State Tax Service of Ukraine, and the Kyiv Metro.
- Nobody on Ukraine’s side has commented on the recent attack, but a public statement may come at a later date
- NoName has a rich history of conducting numerous cyberattacks against Ukraine and its allies since the beginning of the Russian invasion
- The cybercriminal gang first appeared in March 2022, and has been extremely active ever since
- Today, NoName ranks as the most dangerous, resourceful, and motivated cybercriminal group in the world
This recent attack is but one in a string of many that have targeted Ukraine’s cyber-structure over the past 2 years. NoName has resorted to a variety of strategies to discredit the Ukrainian government.
These include disinformation, propaganda, DDoS attacks, and even attempts to silence the Ukrainian mass media. This paints NoName as a multi-dimensional and resourceful organization that cuts no corners when it comes to pushing its goals.
And, as NoName hackers have stated themselves, their goal is to discredit and disrupt both the Ukrainian government and its supporters. This explains why the cybercriminal gang has attacked all of Ukraine’s allies and supporters since the beginning of the war.
NoName’s cybercriminal profile and tactics have made some question its independent status. Some claim that the criminal organization is basically a Russian puppet, controlled by the Russian regime.
While no clear evidence has been uncovered in this sense, the theory still stands.
How NoName Chooses Its Targets
NoName chooses its targets based on its ideological and politically-driven motivations and the hackers seem to be quite well motivated. It’s also important to note that nobody is outside NoName’s reach, no matter their status.
The organization has breached multiple governments and high-end institutions, including the Netherlands, Poland, the US, Germany, France, and even NATO. The latter took place several days ago, when NoName shut off several NATO websites.
But how does NoName operate? The group’s tactics are rather standard for a DDoS actor. The hackers will flood the target website with bot requests, until the network simply can’t handle the load anymore.
This will cause the website to shut off, temporary pausing the victim’s operations. This simple tactic can have significant effects, especially in the case of public services like transportation, banking, and healthcare. Fortunately, most NoName attacks are mild.
This isn’t because the group is incapable of delivering damaging blows but because it chooses not to. NoName is focused on quantity over quality; hit as many targets as possible in a short time span. Naturally, this means sacrificing the quality of the attack.
But the pro-Russian hackers don’t care about that. They only care about making a statement. If it so happens that the breach is more damaging than intended, that’s just a bonus.
NoName also relies on affiliates and collaborates with other pro-Russian cybercriminal groups to conduct more extended operations. These things paint NoName as a fearsome cybercriminal actor that has now become a global threat.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

