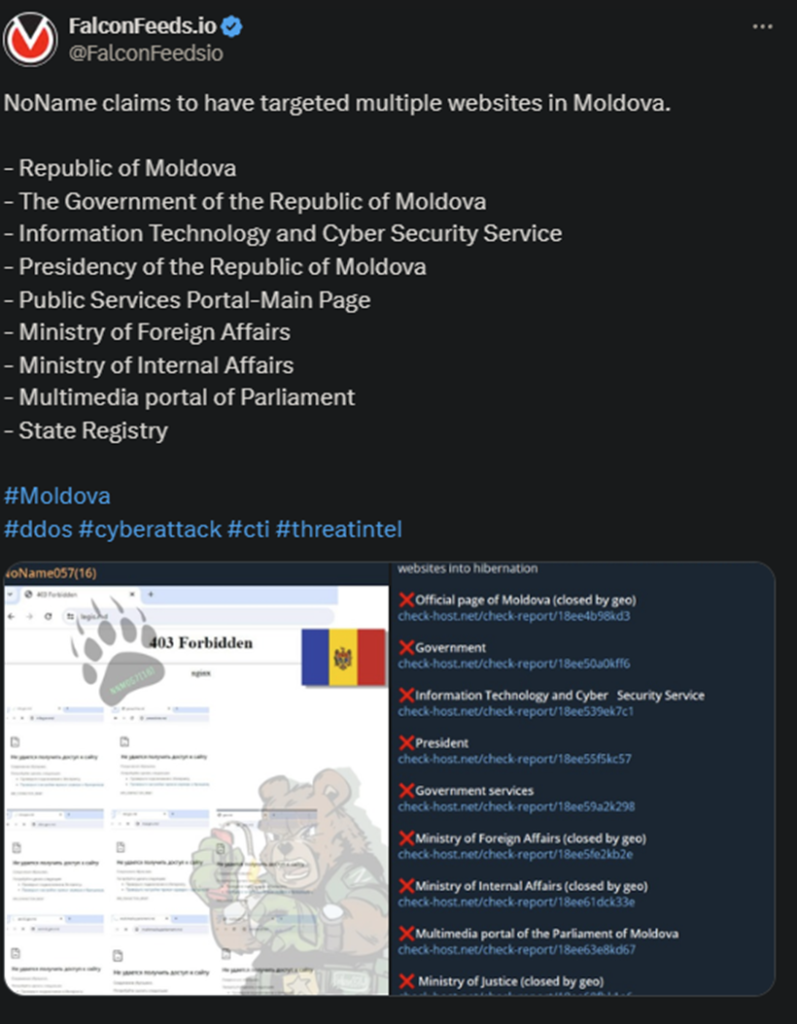
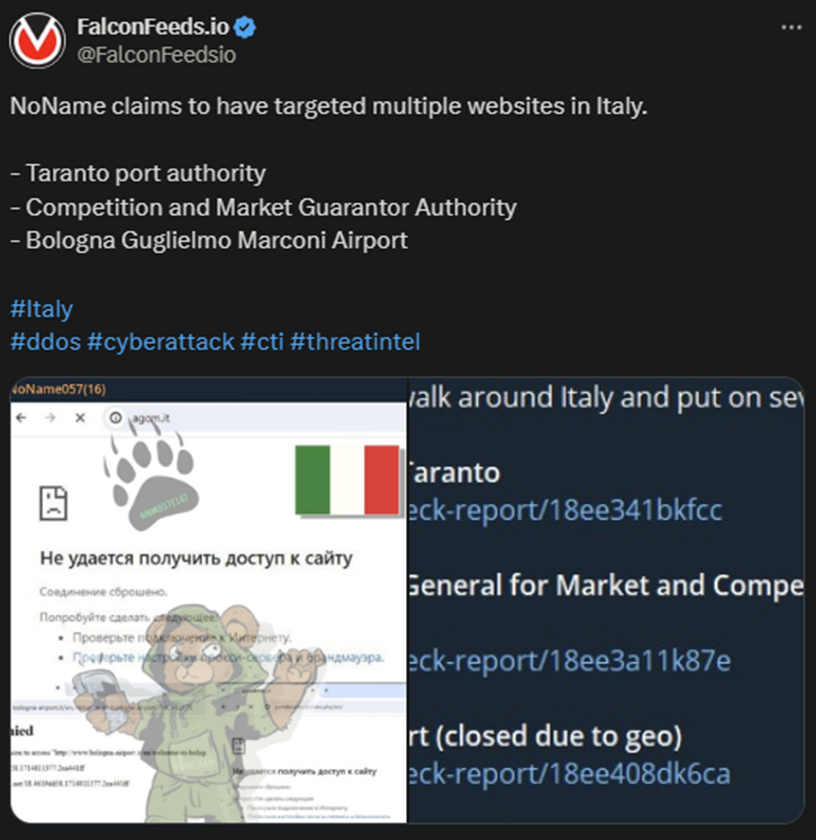
NoName Gets Busy with Moldova and Italy
NoName returns today with another massive DDoS campaign. The string of attacks spread across 2 days and targeted Moldova (yet again) and Italy. The hackers have attached mocking statements to both posts.
- NoName is a world-renowned pro-Russian entity that made it its job to push the Kremlin’s political and ideological goals
- The Moldovan mass media has commented extensively on NoName’s attacks as the government is struggling to find solutions
- Some of NoName’s targets include the Moldovan Ministry of Internal (and Foreign) Affairs, the Moldovan State Registry, and the Italian Taranto Port Authority
- These attacks are part of a larger cybercriminal campaign, during which NoName also joined forces with other cybercriminal actors
NoName’s attacks are typically mild, consisting of targeted DDoS bot floods. The hackers’ trademark DDOSIA tool overwhelms the target website with access requests. These cause the website to become unresponsive, cutting off the access to the main services.
However, the hackers have used multiple MOs to get their message across. These include threats, data leaks, extortion, blackmail, and information war. As to how many of these tactics have actually worked and to what extent; that’s still anyone’s guess.
NoName is an unusual actor, as its first public appearance was at the end of February 2022, shortly after Russia’s invasion of Ukraine. However, unlike other cybercriminal gangs that need time to grow, NoName was already grown.
The group exhibited advanced tactics, capabilities, and funding. They’ve hit multiple targets across just as many countries, with some records mentioning in excess of 2,000 breaches. And NoName’s activity and results have increased with time.
But what does the organization want, and what do we know about it? NoName has been quite elusive so far but extremely proficient at covering its tracks and profile. Let’s see what we know about it.
Is NoName Funded by Russia?
That seems to be a legitimate question, given that NoName operators are interested in one thing and one thing only: pushing Russia’s goals. It’s also interesting to note that the organization isn’t interested in funding, which is why it doesn’t conduct profit-based attacks.
On the other hand, NoName’s operations are not costly. DDoS breaches are fairly simple and cost-effective, and they only inflict temporary blackouts. Most websites are up and running shortly after. But that’s by design.
NoName isn’t interested in inflicting heavy damages, but rather hit as many targets as possible. This is the best way to save costs, made your name known, and spread your message at the same time. This approach can explain NoName’s financial independence.
When it comes to the group’s actual targets, any anti-Russian or pro-Ukrainian organization or governmental institution will do. The hackers are interested in targeting those who send or have promised aid packages to Ukraine.
The goal is to disrupt the flow of funds, equipment, and humanitarian aid into Ukraine. This would give Russia the upper hand in the ongoing conflict.
As a bottom line, while nobody has managed to link NoName to the Russian government, one can’t help but wonder. NoName seems highly invested in Russia’s success to the point of conducting multiple attacks per day for over 2 years now.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

