NoName Keeps its Eyes on Romania
NoName has just announced another DDoS operation against the Romanian government. This comes one day after the infamous gang attacked a Romanian bank with the help of the Russian Cyber Army.
- The hackers announced the hit on their leak platform, mocking the Romanian government, as is typically the case
- NoName justified their attack by blaming Romania for aiding Ukraine in the ongoing war
- The pro-Russian gang ranks as the most active politically-driven cybercriminal organization with multiple victims per day, every day
- This recent operation appears to have been a solo hit by NoName
The NoName hackers wrote in their post that the attack is the result of Romania’s decision to send a Patriot air defense system to Ukraine. This decision was announced by the Romanian president, Klaus Iohannis, on Thursday.
This time, the hackers targeted several prominent public institutions. These include the National Bank of Romania, The Romanian National Cyber Security Directorate, and the Back Deposit Guarantee Fund. Romanian representatives have not commented on the attacks.
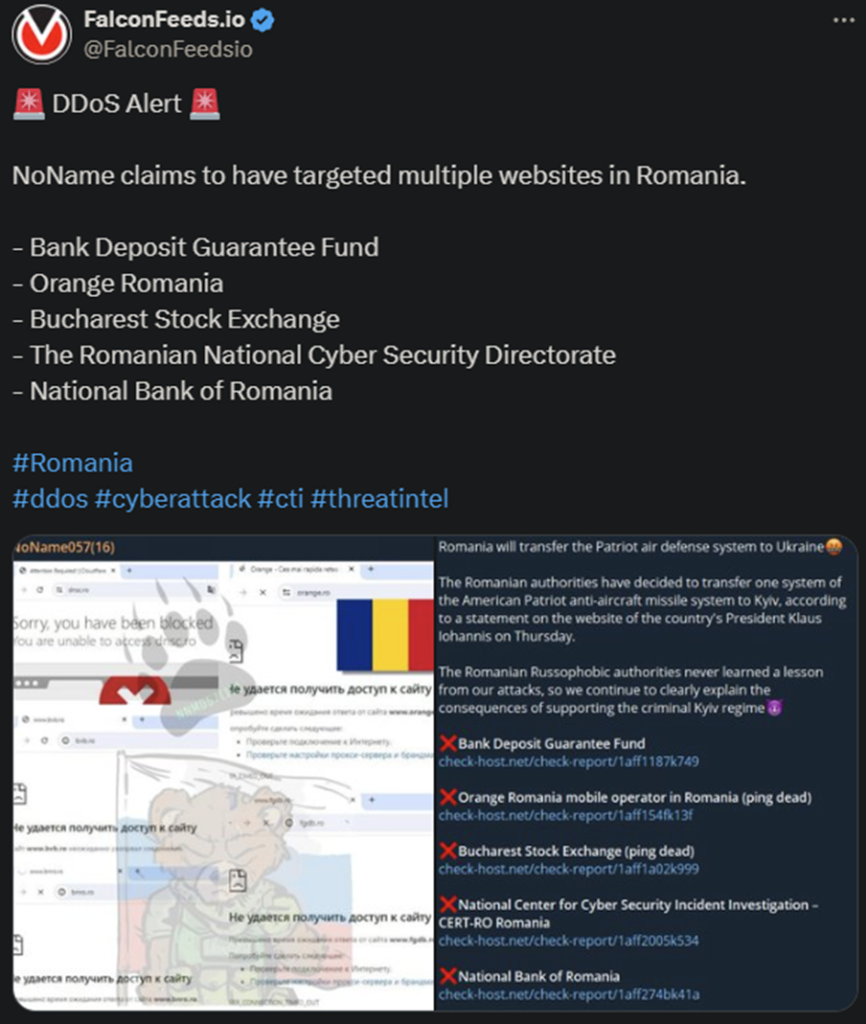
The target websites are currently online, but they were down for several hours following the incident. This was the result of NoName’s targeted DDoS missile, which overwhelmed the websites with access requests. It’s typical NoName MO.
The infamous cybercriminal organization relies on cost-effective operations to disrupt their victims’ activity. The longer the effect, the better, but the hackers don’t invest too much in their attacks.
What are NoName’s Goals?
NoName aims to silence and impact the nations and organizations that they perceive to be Russia’s enemies. NoName became active in February of 2022, immediately after Russia invaded Ukraine.
The hackers have posted their intentions since day one. According to the original post, NoName, the gang aims to “go out on the warpath with Ukrainian sub-hackers and their corrupt servants (…) as well as the Ukrainian grief-hackers who try to support the Neo-Nazi regime of Zelensky.”
Since then, NoName has been extremely active, producing between 1 and 15 victims per day, sometimes spread across several nations. The attacks aim to impact the institution’s online presence and their public services.
In most cases, the attacks manage to take the website offline, which can sometimes have devastating consequences. This is especially true in the case of targeting public transportation or health or emergency services.
It’s important to mention that the NoName hackers use several methods of attack aside from DDoS intrusions. Some of their other tactics include intimidation, public mocking, defamation, spreading propaganda, spreading misinformation, and threatening.
The hackers also join forces with other pro-Russian cybercriminal outlets to coordinate even larger operations. Some of the most notable gangs include KillNet, XakNet, Russian Cyber Army, and Anonymous Russia.
These types of collaborations have allowed NoName operators to impact multiple nations at once. In many cases, the hackers managed to infiltrate several targets in each country, often getting the ‘kill’ count to a dozen or more.
The hackers always prioritize pro-Ukrainian targets, preferably those who are actively involved in the ongoing war. This includes governments and enterprises who have sent or plan to send humanitarian and military aid to the Kyiv regime.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

