NoName Ravages Ukraine
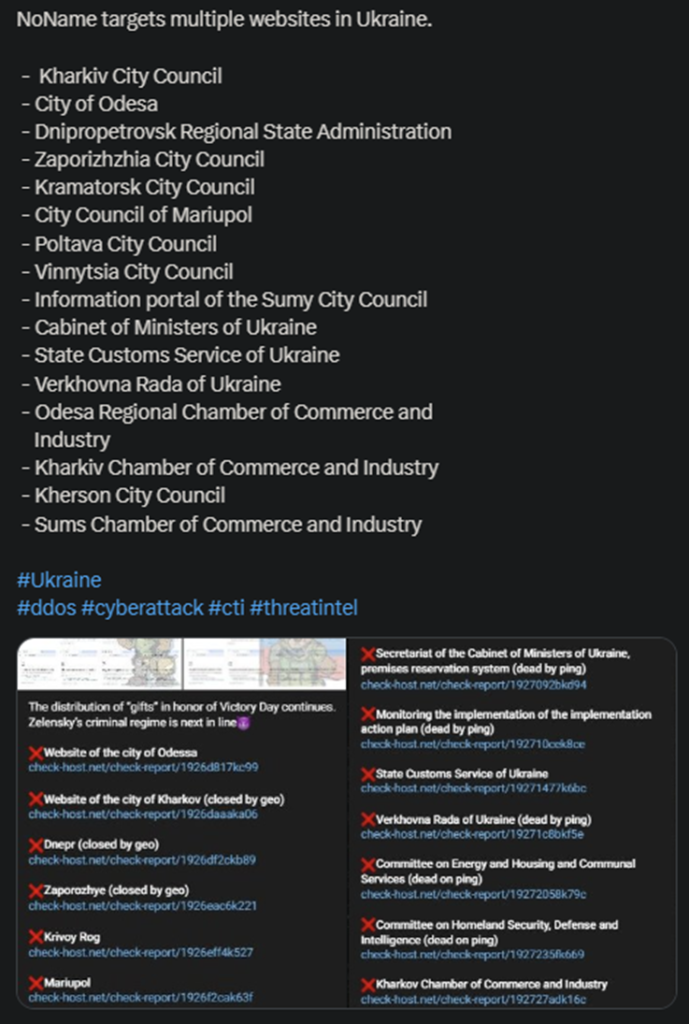
NoName announced a massive operation against Ukrainian targets, managing to bring down no fewer than 16 websites. Some of these include the City Council of Mariupol, the City of Odessa, and the State Customs Service.
- The hackers also published the full list of the victims, along with a mocking note, stating that “Zelensky’s criminal regime” is next
- The attack took place in typical NoName fashion, with the hackers using DDoS missiles to overwhelm the target websites
- NoName is currently the largest and most dangerous pro-Russian cybercriminal gang, operating since February 2022
- The organization aims to push propaganda and attack Russia’s enemies, starting with Ukraine itself
NoName came public shortly after Russia invaded Ukraine and stated its goals clearly from the get-go. The gang aims to support the Moscow regime and target all those who oppose it. This refers primarily to Ukraine, along with all of its allies and supporters.
The group has conducted multiple attacks against Western targets, primarily the US, Poland, the Czech Republic, Ukraine, Romania, Moldova, and others. The attacks are always similar, relying on DDoS bots to flood the target website.
This takes the website offline, directly impacting the target’s online and even brick-and-stone services. Especially if the target manages the public sphere as well.
The DDoS attacks are just part of the problem. NoName has engaged in numerous cyberwarfare strategies to discredit and attack its opponents. These include data theft, blackmail, spreading propaganda, and misinformation war.
The gang has also joined forces with other pro-Russian cybercriminal organizations to conduct more extensive operations. These are generally more devastating in terms of consequences and produce more victims overall.
How to Deal with NoName?
Unfortunately, there’s not much one can do to shield themselves from a DDoS attack. If NoName sets its eyes on a specific organization, it will find a way. The good side of things is that the attacks are generally very mild.
The DDoS fallout is supposed to be mild, because NoName’s goal is to deliver a message. Not spend a lot of resources on more complex and debilitating attacks.
But what makes NoName so scary and effective? Part of the reason is the organization’s almost military-style structure and functioning. Anonymous leakers have stated that NoName functions almost identically to a military organization.
Its members work around the clock, always scanning for potential victims, and have deadlines that they are supposed to meet. These include both time windows and a specific number of targets (typically between 5 and 15 per day.)
This explains, at least partially, NoName’s success and resilience. The other factor worth mentioning is the organization’s spread and funding. The theory is that NoName is a lot more capable, powerful, and well-organized than one would consider normal.
Especially for a newly formed group that proved its worth since day one.
One potential explanation is that NoName is funded by the Russian government itself. This would explain its hardcore pro-Russian stance, elusiveness, and competence. Naturally, nothing has been confirmed so far.
But it’s worth mentioning that the Russian government often supports various pro-Russian cybercriminal gangs. First because it’s financially advantageous and secondly because of the plausible deniability.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

