NoName Snipes the Belgium Government
NoName announced another operation today, this time targeting the Belgium government. The hackers announced several victims within Belgium, namely Proximus, LCL Data Center, Maehdros, Sumatoni, and VOO.
- NoName hackers published a mocking note accompanying the news about the attack
- They accused the Belgian government of Russophobia and called the attack a form of punishment for Belgium’s involvement in the Ruso-Ukrainian conflict
- Belgium has been involved in the ongoing conflict since the beginning, providing the Ukrainian government with invaluable financial support
- NoName is currently the most vocal pro-Russian cybercriminal gang in the world and the most active overall
According to the latest data, Belgium has provided Ukraine with a lot of support over the past 2 years. The Belgian government has provided Ukraine with close to 1.1 billion euros between 2022 and 2024. The 2024 map looks even richer.
While the initial predictions mentioned numbers like 977 million euros as the Belgium’s support since the beginning of the war, that’s only an approximation. The Belgian government itself has boosted that number to 1.7 billion recently.
Furthermore, Belgium has signed another agreement, showing its willingness to deliver another 977 million euros to Ukraine in humanitarian and military aid. It’s understandable why this move didn’t go unnoticed by NoName.
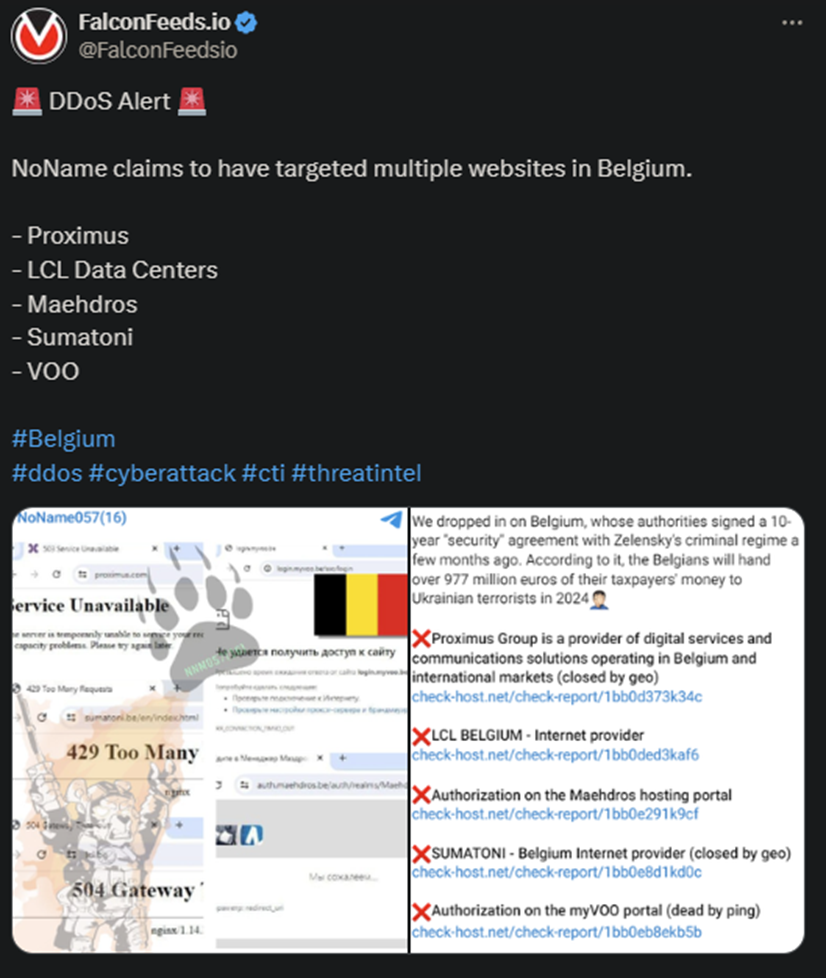
NoName has mentioned the 977-million-euro agreement in their original post, calling the Ukrainian government essentially a band of terrorists. This is typical MO from NoName, which uses a variety of tools to influence the game of war, name-calling being one of them.
Most importantly, Belgium has signed a 10-year agreement with the Kyiv regime, pledging humanitarian and military support for the next decade. Naturally, this only added fuel to the fire.
How NoName Operates
NoName is a pro-Russian cybercriminal gang that first emerged publicly at the end of February, 2022. The date coincided with Russia’s invasion of Ukraine. The hackers immediately stated their support for the Russian regimen and have acted accordingly ever since.
The gang has delivered numerous operations since, touching targets across the Globe. The attacks are always politically and ideologically motivated, with the hackers only targeting pro-Ukrainian targets.
In most cases, the targets are public or governmental institutions, but some private companies have been hit occasionally. It all depends on the victim’s degree of involvement in the Ruso-Ukrainian conflict.
NoName typically prioritizes organizations that support the ongoing conflict directly, either through military means or funding. But they also attack actors that limit their involvement to public support.
It’s important to note that NoName is currently the most active and dangerous pro-Russian cybercriminal entity. The organization scans for and attacks targets daily, sometimes producing multiple victims per day.
This speaks to the gang’s determination and proficiency.
Inside leaks also painted NoName as a quasi-military organization relying on strict deadlines and goals. The gang also uses affiliates and collaborates with other pro-Russian actors to conduct even more intrusive operations.
This allows NoName to remain a Global actor with worldwide reach and seemingly never-ending resources. And while 2023 appeared to be a full year for NoName, 2024 seems to up the stakes even more.
The infamous pro-Russian actor currently ranks as the most active and involved cybercriminal force in the world.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

