Qilin Ransomware Takes a Trip to France
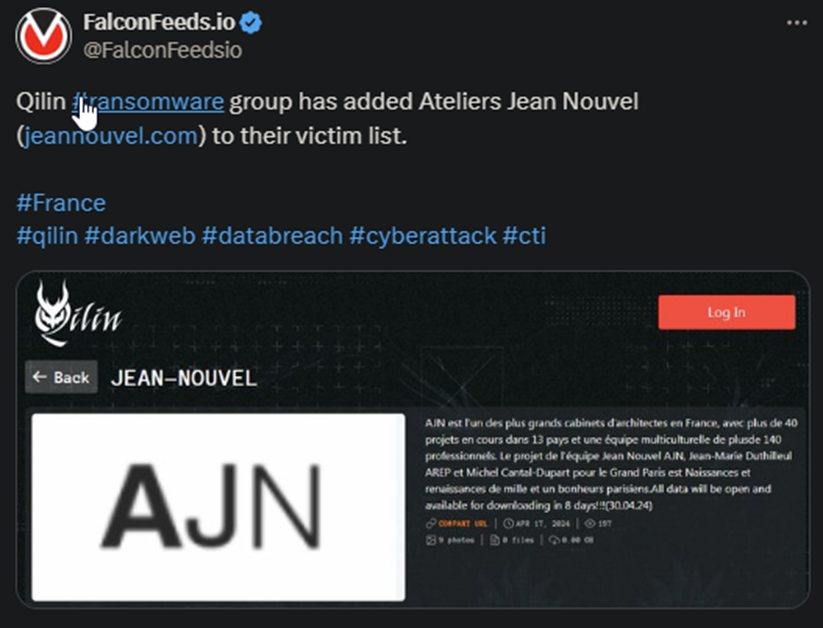
Qilin hackers announced a new victim today on French soil. We’re talking about Ateliers Jean Nouvel, one of the largest groups of architects in France, with more than 40 projects across 13 countries and 140+ professionals behind the wheel.
- Qilin’s post didn’t detail anything about the ransom or how the negotiations are going
- The only thing available on the hackers’ platform is a short summary of the target, along with the 8-day deadline until the stolen data is leaked publicly
- It’s unclear how much data the hackers have been able to steal, but they have posted 9 images showcasing some of it
- Ateliers Jean Nouvel has decided not to comment on the breach
Qilin is a veteran in the ransomware sphere, getting close to 2 years of intense activity. The gang first emerged in July 2022 and grew progressively larger and more influential with time. The organization hasn’t been particularly aggressive, at least not to the level of other actors.
Qilin, also known as Agenda, uses several encryption methods, which explains the difficulty of circumventing the system encryption. The standard MO is relying on the double-extortion practice to increase the leverage during negotiations.
This is good news for Qilin, given that they also work with powerful encryption tools and attack high-value targets primarily. Most importantly, the gang often relies on exposed and vulnerable apps and interfaces to lure in unsuspecting victims.
These features have developed over time and helped Qilin up the food chain. At this moment, the gang ranks as one of the most effective ransomware groups in the world. The only thing that drags its ranking down is its low activity level.
But that’s not necessarily a bad thing for the gang, especially since the operators prioritize high-value targets with healthy revenue pools. This allows them to maximize their profits without exposing themselves too much.
How To Defend Against Qilin?
Qilin isn’t necessarily breaking any ground in terms of tactics and strategies. They’re not the first, nor the last who use legitimate apps and software to create traps. This means that the most basic defense line begins with education.
Learn all of the potential threats and how to avoid them, educate your employees accordingly too, and you should be fine. But the real challenge begins when you’ve already been breached. Because, if you qualify as a high-value target, you will be, sooner or later.
In that case, experts recommend the cold-shoulder approach. Do not negotiate with the hackers, do not contact them for any reason, and, most importantly, do not pay the ransom. The main reason for that is that paying the ransom doesn’t solve anything.
The ransomware operators may still leak the stolen data anyway, if not publicly, at the very least to other cybercriminal actors. You can all guess where that goes from there.
Plus, paying the ransom, or even negotiating with the hackers, automatically marks you as vulnerable. Which means that the hackers will put you on their “to-do-again” list. Which they may or may not share with other ransomware gangs.
The conclusion is clear and intuitive: don’t negotiate, don’t pay anything, move on.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

