The Art of Cyber Deception: Social Engineering in Cybersecurity
Social engineering is behind some of the most crippling cyberattacks in history. It’s the boogeyman of cybersecurity because it’s extremely difficult to guard against.
This phenomenon has reached new heights in 2023, with attacks such as the Equifax data breach and the Twitter Bitcoin scam making headlines around the world.
According to a 2023 Statista survey, 87% of respondent organizations in Sweden say that they’ve lost sensitive information in the past 12 months. Germany sits at 85%, and the US is at 76%.
Globally, 63% of organizations have lost some type of sensitive data as of 2023, which is never-before-heard.
To add to this, most CISOs (Chief Information Security Officers) in the UK (78%) agree that human error is the biggest cyber vulnerability in their organization.
In this article, I will explain everything about social engineering, from the role it plays in cyberattacks to why it works, common tactics, and how to prevent it. I’ll also try to foresee what the future of social engineering brings.
Let’s get started!
Understanding Social Engineering

First, we need to understand what social engineering is and why it works. It’s important to have this foundation before we move on to a more in-depth analysis!
1. What Is Social Engineering?
According to Kaspersky, “Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables”.
So, human error is the core of social engineering. It’s the element that brings everything together.
To succeed in a social engineering attack, hackers need to determine the victim to make an error such as:
- Clicking on an infected link in an email
- Downloading and opening an email attachment
- Opening an infected SMS link
- Replying to a malicious email with sensitive information
And how do hackers convince you to make these mistakes? By spinning a story that you’re likely to believe.
This is when the second core element of social engineering appears – manipulation through deceit.
A good hacker will always try to gather some information about you before attempting to deceive you. They might know you’re a client of bank X or that you’ve recently purchased product Y, for instance.
They gain this information through data leaks, corporate data breaches, or even a phishing attack against you.
And the more information they have about you, the “stronger” their social engineering tactics become.
Through these tactics, hackers can make you:
- Install malware on your device, opening yourself up to more attacks
- Willingly surrender your usernames and passwords
- Send them money
- Become an unknowing money mule for them
But why does social engineering work and why is it so effective against us? Let’s explore that below!
2. The Role of Persuasion, the Illusion of Legitimacy, and Manipulation

Social engineering works through persuasion, the illusion of legitimacy, and manipulation. Here’s how:
- Persuasion
A hacker’s first job in a social engineering attack is to persuade you of their assumed identity. They need you to believe and trust them so you feel safe talking to them.
They’ll employ trust-building tactics, emotional triggers, and exploit various cognitive biases that are so common in humans.
Hackers achieve this by pretending to be someone they’re not and using a fake identity to fool you.
That’s the illusion of legitimacy.
- The Illusion of Legitimacy
Social engineering is effective because it plays on the illusion of legitimacy. Attackers pose as trusted, recognizable entities to earn your confidence and lower your guard.
For example, a hacker might impersonate a representative from your bank—the very institution you already trust with your finances.
When you receive an email or message that appears to come from them, you’re more likely to respond without questioning its authenticity.
Once that trust is established, the attacker can exploit it, guiding you toward actions that compromise your security—like clicking a malicious link, sharing sensitive information, or downloading harmful files.
It’s this manipulation, built on false credibility, that makes social engineering so dangerous.
- Manipulation
Once a hacker convinces you that they’re a legitimate party, they start the final phase of a social engineering attack – manipulation.
It’s time for the hacker to get what they’re after – your money, private data, or access to your device.
They achieve this by manipulating you into clicking on a phishing link, downloading an email attachment, or replying to their email with sensitive information.
Or they could convince you to wire them money through multiple email conversations where they keep manipulating you.
You might notice that all three stages have something in common. That’s right, the target – you.
And you’re a human. That makes you innately vulnerable to social engineering.
Why? Let’s see below!
3. Why Humans Are the Weakest Link in Cybersecurity

The human factor is, by far, the most vulnerable element in any organization, when it comes to cybersecurity.
Here’s why that is:
- We’re Unpredictable
As humans, we often act based on emotions and impulses that go against hard, cold facts and our better judgments.
Plus, everyone acts differently when presented with the same information or situation. You might think that an email is likely a scam while I might believe it’s legitimate.
You might be less convinced when the hacker seems to know personal details about you, while I might be fully persuaded to trust them.
This unpredictability in acting and reacting is what hackers rely on to manipulate us through social engineering
- We Want to Trust Each Other
According to neuroscience, humans are innately inclined to trust one another. While this might seem poetic, it’s quite a disadvantage when talking cybersecurity.
When others are out to deceive us, we’re naturally predisposed to trust them. It takes a conscious effort to distrust someone, so more work for our brains.
It’s easier to trust someone rather than distrust them, is what I’m saying. If the hacker gives us conscious reasons to trust them, that makes the job even easier for our brains.
- We’re Flooded with Information
In 2023, information is everywhere, on our phone, on the websites we visit, on our email, and so on.
We’re flooded with tons of information daily, and it becomes harder to discern truth from lies. To us, a scam email might seem like just another piece of information like all the others.
If you work in a corporation, this aspect becomes more relevant as there’s also internal communication to account for.
Emails, text messages, Slack, Microsoft Teams, there’s information coming from every direction that overwhelms us and leads to a routine behavior.
It’s easier for a hacker to deceive you by hiding among this flux of information and exploiting your lack of attention.
4. Six Principles of Social Engineering

To better explain how social engineering works, we’ll use Dr. Robert Cialdini’s Six Principles of Influence, which apply perfectly to cybersecurity:
I. Authority – We tend to be more trusting toward people who seem to know more than us or occupy a higher social/professional position
II. Reciprocity – We feel an internal obligation to respond in kind when we receive a gift or a sign of goodwill from others
III. Consistency – We like to remain consistent and follow through with what we’ve already decided. If a hacker convinces us to agree to something small, we’re more easily convinced to do something bigger next time
IV. Liking – When we like someone, we tend to more easily agree to whatever they ask of us. Impersonation is the strategy that uses this principle in social engineering
V. Consensus – We’re more likely to agree to something if we know that other people are also doing it. We like to be in a consensus with everyone else
VI. Scarcity – The less common something is, the more value we put on it. In our minds, it’s more valuable because not everyone can have it
You can track these principles across all social engineering cyber-scams, whether it’s an email scam, a phishing attempt, and so on.
Psychology is the core element of social engineering, and that’s exactly why it’s so successful. They exploit key vulnerabilities in the way we think, act, and react to various information and contexts.
The most commonly-used principles are Authority and Liking, when hackers impersonate people of authority or people who are generally well-liked in society. They’ll make demands in their name, hoping that the victim agrees.
In many cases, the victim falls prey to these scams simply because they’re fooled by these principles acting in their subconscious.
But enough about that. Let’s talk about something more substantial and see how hackers use social engineering for specific attack types!
Common Techniques and Tactics

It’s time we had a look at specific techniques and tactics used by criminals when launching social engineering cyberattacks.
You’ve likely seen most of these tactics in action or heard about them. But you don’t know their name.
No worries! Let’s go through them now.
1. Phishing Attacks
Phishing attacks have become increasingly common, and they rely almost entirely on social engineering. I’ve talked about why phishing attacks are so common in another article. You can read it here.
Here’s how phishing attacks work, in a nutshell:
- Assumed Legitimacy – The hacker pretends to be someone you trust and respect, like an institution or company
- The Hook – The hacker comes up with a reason why you should click on a link, download an attachment, or provide them with personal data (renewing your subscription, changing your security settings, etc.)
- The Solution – The hacker gives you a link, attachment, or another infected element that can solve your previously-stated problem
- The Deceit – Once you click on the infected link, you’ll be redirected to a fake website that’s designed to look as much as possible as the original
With these four elements, a hacker transforms a phishing attack from a simple cyberattack into a global epidemic that affects millions of users.
There are multiple types of phishing attacks, including voice phishing, email phishing, SMS phishing, spear phishing, whale phishing, and more.
It’s one of the most varied, effective, and dangerous cyberattacks, and it’s largely due to the social engineering factor.
2. Pretexting
A pretexting attack implies that the attacker assumes a fake identity that’s within your expectation to communicate with.
For instance, they may impersonate a company employee from another department, asking you for some documents because they need them for “something” (insert justified reason here).
That “something” could actually be a valid event in the company if the hacker managed to gain access to internal communications or had prior knowledge.
This pretext is often enough for many to fall victim to this attack. They won’t question the hacker’s assumed identity and won’t think to double-check.
The communication with the hacker was something expected given the pretext invoked by the hacker.
3. Baiting
Baiting attacks are really tricky but thankfully, easy to avoid. The hacker uses your curiosity to make you install an infected software, download an attachment, or insert an infected flash drive in your device.
They may leave these thumb drives in conspicuous areas where they’ll be found by victims. These thumb drives might have official labels on them to pique your interest even more.
This works digitally as well. Think of an email talking about a money-making program that guarantees constant earnings every month. Is your interest piqued yet?
Yeah, that’s what hackers are relying on. They’ll first give you the bait, and if you take it, they’ll begin the attacks.
4. Tailgating
Tailgating is strictly a physical attack that uses social engineering to convince an authorized employee to allow the hacker access into a restricted area.
Usually, the hacker will impersonate someone else or provide a justified reason for why they need access to the restricted area.
Pretexting is often used as part of a tailgating attack to reinforce the belief that the hacker has legitimate reasons to access the restricted area.
5. Impersonation
Impersonation attacks rely on the attacker assuming a fake identity and fooling you with it. The fake identity is the core element of this attack.
The hacker could pretend to be a trusted contact, an authority figure, a technical expert, a bank representative, or anything else that might trick you.
The goal is to gain your trust by appealing to your tendency to unconsciously trust certain figures or individuals.
6. Quid Pro Quo
Quid pro quo means “something for something” in Latin, and that’s exactly how a hacker carries out this attack.
They’ll assume a fake identity and pretend to offer you something in exchange for various things like:
- Your personal data
- Completing a survey
- Downloading an attachment and reading it for feedback
Most often, they’ll offer you money in exchange for your “service” to them. They come off as trustworthy because it’s a transaction. You don’t give away anything for free.
Moreover, you feel somewhat obliged to give something to them in return after they promise to pay you.
Real-Word Examples of Social Engineering Attacks
Case Study 1: BEC Attack on Google and Facebook
Between 2013 – 2015, Evaldas Rimasauskas (the perpetrator) impersonated Quanta Computer, a Taiwanese electronics manufacturer that was cooperating with Google and Facebook.
They sent phishing emails to employees at both companies, asking for payments for goods and services.
Both companies wired the money, and Rimasauskas moved it to various bank accounts around the world.
By the time he was caught, he had swindled around $100 million from Google and Facebook. He managed to do this by forging the signatures of the companies’ executives on the letters, invoices, and contracts that he had sent to the banks.
This was a classic case of impersonation and business email compromise (BEC) that made the headlines back then.
Case Study 2: CEO Fraud Attack on Austrian Aircraft Parts Maker FACC
FACC, an Austrian aircraft parts maker suffered a CEO fraud attack in 2016, losing around $47 million. CEO fraud is the same thing as business email compromise but in this case, the company was targeted with a spear-phishing attack.
The hacker impersonated the CEO, Walter Stephan, and sent a fake email to the financial department, asking them to wire 50 million euros to an account.
They justified the transfer as part of the company’s recent acquisition projects, so the financial department didn’t see anything wrong with it.
After the company realized the trickery, they managed to stop a transfer of 10.9 million euros but they still lost 39.1 million euros.
This was a classic social engineering attack where the hacker had prior info and used impersonation tactics to manipulate the victims into sending them the money
Case Study 3: The Art of Influence in the Twitter Bitcoin Scam
The Twitter Bitcoin scam is now one of the most infamous cyberattacks in history due to its odd nature.
On a sunny afternoon in 2020, Twitter was flooded by tweets from big names such as Elon Musk, Kanye West, Bill Gates, Joe Biden, and Barrack Obama, promising to send you double the amount of Bitcoin you’d sent to their accounts.
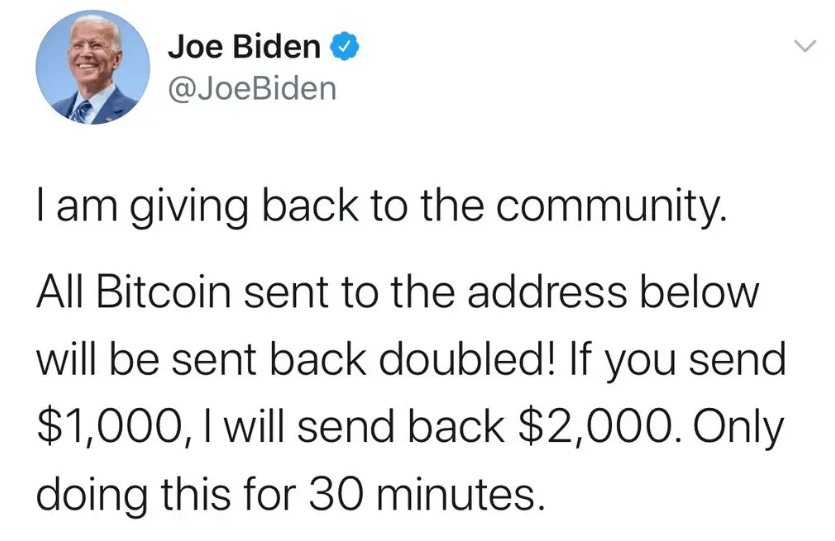
https://www.nytimes.com/2020/07/15/technology/twitter-hack-bill-gates-elon-musk.html
Naturally, this was all a large-scale scam operation put together by a few attackers. Twitter was eventually forced to disable several of its services, including the tweeting function of verified users, for some time.
The cause of this brazen attack was a social engineering attack targeting several of Twitter’s employees. The attackers gained access to the company’s internal systems and managed to hijack the accounts of high-profile accounts.
By the time the scam was revealed, the scammers had received over $100,000 in Bitcoin, all of which was lost forever in the blockchain.
Red Flags and Prevention

It’s not all bad, though. There are ways to spot a social engineering attack before you fall victim to it.
Below, I’ll take you through the most common red flags and best practices you should follow to avoid social engineering attacks.
1. How to Spot Social Engineering Attempts
There isn’t a foolproof way of spotting a social engineering attack but if you check multiple boxes below, then you’re likely dealing with a scam.
Let’s go through some of the most important red flags of social engineering attacks:
I. Unexpected Messages
When you first open that email, ask yourself – “Am I expecting an email on this topic?”. While some phishing attacks hijack expected communications, most don’t follow this pattern.
That’s because most hackers don’t know anything about their victims and haven’t gathered any info on you.
So, they’ll try their luck with general scam emails. These could be:
- Banking emails about security breaches
- Winning an inheritance from some old granny who’s decided to donate her fortune to you
- Being the winner of an ultra-expensive course on cybersecurity (this happened to me)
Even if the topic of the email is somewhat of interest to you, were you really expecting it? In most cases, the answer is “no”.
Then, there are situations when you’re told you’ve won some lottery that you didn’t even participate in. That’s a clear scam.
If you’re not expecting the email, that should raise your awareness a bit. It doesn’t necessarily mean that it’s a scam, since many legitimate communications come unannounced, but you should exercise caution from that point on.
II. Unexpected Request or Demand
Does the sender ask something of you that isn’t expected or natural? Perhaps it’s something you’ve never done before, like:
- Sending them information that they’ve never asked before (if they’re impersonating someone you know)
- Sending them money for an utterly odd reason
- Run an executable on your device, even though this request comes out of nowhere and the reason is shabby at best
- Open a random document that you know nothing about
If the other party is asking you to do something you’ve never done before or that you’d normally strongly consider before doing, you should think twice before agreeing.
When impersonating people we know, hackers user the unconscious familiarity and trust we have toward the other person to manipulate us into agreeing with unreasonable requests.
III. Suspicious Attachments or URLs
Most social engineering attacks will include an infected attachment in the email and they’ll try to trick you into opening it.
Or they could include hyperlinked URLs in the body of the email, and ask you to click on them.
Here are a few examples:
- “We’ve detected a suspicious activity. Click HERE to visit your account and confirm that it was you”
- “You’re the lucky winner of an RTX 2080 graphics card. Visit our shop through the following link to claim your prize”
- “We’ve attached a copy of the document you requested, so feel free to open it at your leisure”
Any one of these links and/or attachments could be infected, so you have to be extremely careful what you click or open in the body of the email.
IV. Spoofed Hyperlinks and Websites
A very effective way of spotting a scam hyperlink in an email is to hover with your mouse over it and read the address.
Does the address match the text of the hyperlink and text before you click on it? If it looks different, then you’re dealing with a spoofed hyperlink.
They made the text look legitimate but didn’t bother to change the actual website address, hoping you won’t check it.
Then, there are situations when the address looks 99% identical to the real thing. These are complex social engineering attacks that are harder to spot.
Remember one thing – the hackers cannot 100% copy a legitimate site’s URL address or domain name. They have to change something. For instance:
- “https://www.paypalhome/us/home” instead of “https://www.paypal.com/us/home”. The addition of elements like “home” in the URL address is how hackers spoof legitimate websites
- “https://www.gov.florida” instead of “https://www.usa.gov/states/florida”. The link clearly looks different but you might not know what the legitimate link looks like
Sometimes, the domain name might be intentionally misspelled in the hope that you won’t notice. Especially if it’s a website you’ve visited many times in the past.
By now, you either don’t check the URL or you easily ignore mistakes without taking notice.
V. An Offer That’s Too Good to Be True
Is the email offering you something that sounds too good to be true? Trust me, I’ve researched cyberattacks enough to know that there’s no such thing as a legitimate offer that’s too good to be true.
They’re all scams in disguise. There’s no one who’ll donate a few million dollars to you, a random person who hasn’t done anything to earn it.
Even if you’re promised money in exchange for your information or something of that nature, don’t fall for it. There’s no such thing (in most cases).
Other social engineering scams promise to send you a certain sum of money but you’ll have to pay the transaction costs, which are insignificant compared to the sum you’d receive.
But you won’t receive anything because it’s a scam. You’ll simply pay the transaction costs and that’s it. The hackers will have extorted you of some money in exchange for a fake promise.
VI. The Urgency of the Email
If the subject of the email looks to be very urgent and it’s putting pressure on you to act quickly, think twice before clicking on any link or opening any attachment.
Hackers rely on psychological pressure to manipulate you into acting quickly without double-checking. Either out of fear, greed, or FOMO, social engineering works in many wondrous ways.
Here’s how these emails might look:
- “Don’t miss this chance to win $30,000 in the annual Florida lottery. You’ve been automatically screened for participation! This offer will expire in ONE HOUR!!”
- “WARNING! We’ve detected suspicious activity in your account. Please click here to change your password and secure your account right away!”
- “We regret to inform you that your account has recently been part of a data breach. If you do not want your funds to be at risk, please click this link to secure your account”
Try to not let your emotions get the better of you. Stay calm and take a moment to analyze the email. Most times, there’ll be some bad spelling or another red flag present.
VII. Bad Spelling
Bad spelling is often the first thing you see when dealing with a social engineering attack. You see, English is often not the hackers’ first language, so they struggle to speak it correctly.
So, they’ll make grammar mistakes, spelling mistakes, or speak in a non-professional manner that isn’t normal for a professional company.
You’ll easily spot mistakes like:
- “Clic” instead of “Click”
- “Acount” instead of “Account”’
- Inconsistent formatting of sentences and phrases
- Bad sentence structure
Reputable companies always have proofreaders checking their emails before being sent. Think about the last time you’ve spotted any such mistake in a legitimate email.
They’re very uncommon to the point of being non-existent. Companies know that these types of mistakes make them look unprofessional and sloppy, and that’s the last idea they want to transmit to their customers.
VIII. Generic Greeting and Empty Signature Section
Check the introduction to the email. Is it generic or specific? A legitimate company that has a good reason to contact you should know your name, at the very least. And they should use it in the greeting section.
If all you see is a generic “Dear Sir/Madam” or “Greetings, Valued Customer”, then it’s highly likely that you’re dealing with a phishing scam. Hackers generally don’t know their victims’ names or other personal information. That’s what they’re trying to get from you.
Instead, they build generic-looking emails and send them en masse to all the email addresses they’ve stolen, hoping that something sticks.
You should also check the signature section toward the end of the email. Do they provide any contact information like a phone number or a customer support email address?
If there’s nothing there, there’s all the more reason to suspect the worst.
Most social engineering scams are easy to spot if you check all the boxes on this list. However, some are exceptionally well done and it’s much harder to avoid them.
It’s not impossible, though. Emphasize cybersecurity education and best security practices to improve your overall security!
2. Educating Employees on Social Engineering Attempts

Social engineering attacks can be disastrous for a company with a reputation to defend. Falling prey to a data breach can lose you the trust of your clients and put your financial situation at risk.
Fortunately, there’s one major element of defense against social engineering attacks that you can control – your employees.
Often, employees are your last line of defense against these tricky attacks. They’re also the weakest link in your security system.
If an employee installs an infected software on the company device, which then spreads throughout the company network, you’re in big trouble.
That’s why educating your employee in cybersecurity and social engineering, especially, is essential.
Here are a few tips on social engineering training for your employees:
I. Basic Understanding of Social Engineering
First, you should teach your employees about the principles of social engineering. What it is, how it looks in the real world, etc.
Use real-world examples of actual social engineering attacks to exemplify how the data breaches used social engineering for a successful infiltration of the company systems.
Emphasize the idea that social engineering relies on manipulation, deception, and the illusion of legitimacy to catch victims unaware.
II. Common Social Engineering Tactics
Teach your employees about the most common cyberattack types that use social engineering.
We’ve already talked about these but here’s the list, in any case:
- Phishing emails
- Pretexting
- Baiting
- Tailgating
- Impersonation
- Quid pro Quo
Awareness is the name of the game here. Your employees should become aware of what to look out for. By knowing how social engineering attacks look, they’ll know how to avoid them.
III. Keeping Calm and Identifying Red Flags
It’s important to hammer down the idea that no matter how urgent a communication may sound, employee should remain calm and not make rash decisions.
Even if an email comes from the CEO, asking for an urgent money transfer, the financial department should first verify the authenticity of the email.
If it’s a phishing scam, there will likely be red flags. Misspellings, grammar mistakes, an unusual request, anything that seems odd and out-of-place – employees shouldn’t ignore it.
And even if there aren’t any red flags, they should still contact the other party using the usual contact details (not the ones provided in the email) for confirmation.
IV. Reporting Suspicious Activities
Make it clear to your employees that they should report anything that seems out-of-place or suspicious.
It doesn’t matter if it’s a marketing ad for baldness treatment or an unexpected SMS text on the work phone, they should all be reported at once.
These events could be scamming attempts by hackers who managed to get their hands on the company’s contact details.
Or they could reveal that an employee’s work phone has been breached and company data is put at risk.
Even if your employees don’t see the merit of reporting every minor suspicious activity to higher-ups, emphasize its importance.
Your security officer might be able to glean more information from a seemingly minor reported event than the employee who reported it.
V. Enforce Strict Cybersecurity Policies
Regardless of what cybersecurity policies you enforce, make sure all your employees are familiar with them and stick to them at all times.
You might need to perform regular evaluations to ensure that all employees adhere to the policies but that’s a price you should be glad to pay.
Otherwise, the consequences of a cyberattack caused by an unaware employee could cost you a lot more.
Employee awareness and adherence to cybersecurity policies make up the foundation of an organization’s cyber-security.
VI. Convey the Consequences of a Cyberattack Clearly
Lastly, you should be painstakingly clear about the consequences of a social engineering attack caused by employee lack of awareness.
Both the organization and the employee in question will have a lot to lose from a cyberattack.
This should motivate your employees to remain vigilant at all times. After all, when the consequences extend to them, that’s all the more reason to be careful.
They’ll be just as motivated as you to prevent a social engineering attack if they don’t want to be demoted or worse.
But what else can you do to stop social engineering attacks dead in their tracks?
Let’s see below!
3. Cybersecurity Best Practices

Fortunately, there are actionable tips you can implement to avoid or prevent social engineering attacks.
Before that, though, I should re-emphasize that awareness is the best protection against social engineering attacks.
This means knowing:
- What social engineering is and its principles
- How different social engineering attacks work
- How to spot a social engineering attack based on the red flags you find
Enough with the general info, though. Let me give you actionable best practices for keeping you or your company safe from social engineering attacks:
I. Set the Spam Filters to High
All email providers have spam filters, and they’re there for a reason. So, use them. Set them to “High” to filter out the vast majority of phishing emails.
A word of caution, though – this might put some legitimate emails into your Spam folder too, so you might want to check for this.
Moreover, spam filters won’t stop all social engineering attacks. Some will simply avoid the filters altogether and get to your inbox.
And knowing that your spam filters are set to max, you might start thinking that whatever reaches your inbox is safe.
It’s not.
Don’t let the spam filters lull you into a false sense of security because they’re not foolproof. If they were, cybersecurity would be a lot simpler and cybercrime a lot less dangerous.
II. Never Provide Personal Information Over Email Unless You’re 100% Sure
I can safely say no legitimate company will ever ask you for personal or sensitive information over email unless it’s really general information for confirmation purposes.
The rule of thumb is this – whenever an email asks you for personal information, don’t give it to them until you’ve fully established the other party has a legitimate reason to ask for it and that they’re a legitimate company.
Many times, hackers come up with pretty good justifications for why they need your information. But don’t let this fool you.
They might sound convincing but that shouldn’t be enough to deter your suspicions. You need foolproof evidence that they are who they say they are.
Here’s how you can get that evidence:
- Look for that company online and search for their contact details. Then, contact them using the official info and ask them about the email you received
- Compare their official contact details with those provided in the email, or with the sender email address
It’s not feasible to do this for every single email you receive but you don’t have to. Only do this for emails who ask you for personal or sensitive information.
I guarantee you there won’t be too many of those who are legitimate.
III. Implement Multi-Factor Authentication
Multi-factor authentication is the bread and butter of robust cybersecurity. It ensures that employees with privileged access aren’t a surefire vulnerability even if they fall prey to a phishing attack.
Biometrics and OTP are starter-level MFA but they’re not exactly foolproof or even robust. They’re somewhat good as additional security mechanisms to prevent unauthorized access.
Even if a hacker manages to get access credentials for an employee through social engineering, they won’t be able to access company assets without access to that employee’s device.
However, both biometrics and OTP codes vulnerable to social engineering phishing attacks. Malicious actors can intercept these quite easily.
If you need an airtight MFA system in place, I recommend a physical security key like YubiKey or one of its alternatives. They’re the golden standard when it comes to 2-Factor Authentication.
I’ll have a guide on physical security keys up pretty soon, so stay tuned to PrivacyAffairs for more info on them!
IV. Implement the Principle of Least Privilege
The Principle of Least Privilege is part of the Zero Trust security model, and it prevents Privilege Creep while ensuring employees can’t access resources they’re not supposed to access.
Essentially, it minimizes the impact of a potential data breach caused by employee lack of awareness.
Even if a social engineering attack succeeds, the employee won’t put the entire company at risk because their privileges are limited by the Principle of Least Privilege.
I’ve explained how to implement the Principle of Least Privilege in another guide, so make sure to check that out for extra details!
The idea is to provide every employee only with the least privilege they need to complete their tasks.
You should enforce this company-wide and conduct regular assessments to ensure that there are no deviations from this principle.
These assessments will be essential in preventing Privilege Creep, where employees have higher-than-necessary temporary privileges that are not revoked.
V. Validate All Endpoint Devices
While Multi-Factor Authentication and the Principle of Least Privilege are a good start for defending against social engineering attacks, they’re not enough.
To avoid unauthorized access from foreign devices, you should implement required validation for all endpoint devices connected to the company network.
No pre-validated devices should be allowed to access the network, even if they have the right credentials.
If a foreign device is trying to connect to the network, their access should be suspended until validated.
With this, you’ll have another security countermeasure in place in case everything else fails. This is especially important when BYOD policies are in effect.
You should assume that any employee could and will fall prey to a social engineering attack at some point. Expecting the worst will help you prepare better for a cyberattack.
Validating all endpoint devices will also help you identify which device was used to cause a data breach, if an attacker hijacked an employee device for the attack.
Following these 5 cybersecurity best practices should put you ahead of most social engineering attacks!
VI. Get Cyber Insurance
I’ve written a comprehensive guide on cyber insurance already, so you can go read it for more details.
To summarize, here are the main benefits of cyber insurance:
- Protection against cyber risks by offering timely assistance in mitigating cyberattacks
- Network-wide security coverage against any cyber threats, including cyber terrorism
- Coverage for financial damage occurring because of cyberattacks, including fees for investigations, legal responsibilities, credit monitoring services, and more
- Compensation for business interruption or loss of revenue in the case of a cyberattack
- Legal assistance in the aftermath of a cyberattack, paying for legal counsel and any lawsuits that appear because of privacy violations or data breaches
- Guarantee of the financial stability of a business even in the event of severe cyberattacks
- Improve the reputation of a business by highlighting their dedication to protecting client data
Most cyber insurance cover social engineering attacks but there are some things they don’t cover. One of them is human error. If the attack happens because of your employees, then the insurance is null.
But there are still many use cases for a cyber insurance. And you’ll have to rehash specific details with your insurer to find out what they do and don’t cover.
The Future of Social Engineering

We’re nearing the end of this guide, but before we wrap up, I want to provide a prospective analysis of social engineering in the coming years.
We’re already witnessing several emerging trends and tactics used by hackers that could significantly alter the landscape of cybersecurity.
Below, I’ll explore some of these developments and discuss their potential impact on the future!
1. Emerging Trends and Tactics
The recent years brought about many changes in social engineering. Here are the essential trends I was able to identify:
I. Business Email Compromise Attacks Are Getting More Costly
Business Email Compromise attacks (BEC) are some of the most common social engineering attacks.
They’re also among the most damaging ones, according to the FBI. It’s easy to see why, too. They deal exclusively in financial theft.
Digital Guardian said that BEC attacks cost businesses around $80,000 on average in Q2 2020, up from $54,000 in Q1.
As of May 2023, the second-most common type of BEC scams targeted payroll information, with the most common involving luring.
Also, here’s a Statista table that shows the distribution of BEC attacks worldwide from January to April 2023:
| Type of BEC Attack | Percentage of Attacks |
| Lure | 62.35% |
| Payroll | 14.87% |
| Invoice | 8.29% |
| Gift Card | 4.87% |
| Business Information | 4.4% |
| Other | 5.22% |
Luring involves baiting the target to a fake login page or luring them into making wire transfers via Zoom meetings.
They impersonate the company’s CEO or another high-profile executive in the company, use their profile picture, and start a zoom call. They’ll blame technical issues on the lack of video and ask the victim to make urgent wire transfers.
Clearly, BEC scams are getting more and more damaging to companies around the world. This warrants more awareness from all market players and organizations.
II. State-Sponsored Social Engineering Attacks Are Growing in Number
State-sponsored attacks (SSA) are cyberattacks officially linked to a nation-state. They occur for three reasons:
- Obtain intelligence on the victim
- Exploit vulnerabilities in the infrastructure
- Exploit people and systems for financial gain
Back in 2020, during the COVID-19 pandemic, there have been identified several nation-state campaigns to steal COVID research data.
In the same year, Microsoft released its annual “Digital Defense Report” that uses data from over 1.2 billion PCs, servers, and devices. All in all, around 1.8 petabytes (1.8 million GBs) of data.
They found that state attackers were shifting their attention from malware-based attacks to social engineering-based attacks like BEC, phishing, and credential stuffing.
https://blogs.microsoft.com/on-the-issues/2020/09/29/microsoft-digital-defense-report-cyber-threats/
Here’s what Tom Burt, Microsoft’s VP of Customer Security and Trust, had to say:
“In past years, cybercriminals focused on malware attacks. More recently, they have shifted their focus to phishing attacks (~70%) as a more direct means to achieve their goals of harvesting people’s credentials. To trick people into giving up their credentials, attackers often send emails imitating top brands.”
This is yet another worry for organizations around the world but it’s great that we have this data to raise awareness about it!
III. Expansion of the Phishing-as-a-Service Market
The Cybercrime-as-a-Service phenomenon (which includes Phishing-as-a-Service) has evolved beyond our wildest expectations in recent years.
Cybercriminals can get their hands on phishing toolkits for as little as $50, according to the security firm Cyren.
Their research lab has found 5,334 unique phishing kits deployed online (as of 2019), and that number has likely grown disproportionately ever since.
The attraction of phishing-as-a-service is obvious – lower technical skill requirements for attackers. Being able to pay for a ready-to-use cyberattack kit has forever changed the cybersecurity landscape.
In 2021, ZDNet reported on a brand-new phishing tool called LogoKit that could adapt a phishing attack “in real time to adapt to targeted victims”. It would change the logos and text on the page seamlessly depending on the website the victim wants to access.
According to ZDNet, LogoKit was installed on more than 300 domains and over 700 websites at the time of writing their article.
Here’s how LogoKit works, in a nutshell:
- It sends users a phishing link leading to a fake authentication page mimicking the intended website’s auth page
- Once the users access the infected link, LogoKit automatically obtains the intended company’s logo from a third-party service like Google’s favicon database
- It positions the logo seamlessly at the top of the login page
- It auto-completes the user’s email address in the email address field, creating the impression that the user has previously logged into the site
- Once the victim enters their password, LogoKit makes an AJAX request, sends the victim’s email address and password to an external source, and redirects them to the legitimate company website
This entire process happens seamlessly, without the hacker’s continued input. Moreover, the kid is very modular and customizable, so it works on a wide variety of websites.
It also doesn’t rely on pixel-perfect templates to mimic a website’s authentication page, instead using embedded JavaScript functions that are easier to use.
Are you paranoid yet? Yeah, me too.
And remember, this was in 2021. Think about what hackers could achieve with Artificial Intelligence and machine learning…
IV. SIM Swapping
SIM swapping, also known as SIM hijacking or SIM swap fraud, is a growing cyberattack that relies entirely on social engineering.
The attacker will convince the victim’s mobile service provider to port the victim’s phone number to another SIM card (that is in the hacker’s possession).
Then, when the victim uses 2FA to access accounts associated with that phone number, the hacker receives the codes and is able to access the victim’s accounts.
This lets the hacker access:
- Bank accounts
- Emails
- Text messages
- Social media profiles
The FBI reported in 2021 that hackers were able to make $68 million from SIM swapping scams in that year alone.
Comparatively, from 2018 to 2020, victims suffered around $12 million in financial losses. This was almost a 7x increase in financial damages from the 2018 – 2020 period to 2021.
But averaging out the $12 million per year, we end up with $4 million in SIM swapping damages per year in 2018, 2019, and 2020.
In 2021, the total damage in SIM swapping was $68 million, which is a 9.5 increase per year. And this was in 2021. We’re almost in 2024, and those numbers should have gone up significantly more with the AI revolution.
Clearly, SIM swapping cases are becoming more damaging, more common, and more financially disastrous over the years.
I’ll probably dedicate a guide on SIM swapping attack patterns and prevention methods in the future, so stay tuned!
2. AI and Automation in Social Engineering & Other Cyberattacks

The recent technological boom in Artificial Intelligence and Machine Learning opens up entirely new avenues of attack for cyber terrorists.
One such attack method that has consistently evolved in recent years is deepfaking. While it’s often used for entertainment purposes, one cannot ignore its obvious manipulation potential.
A University College London study published in 2020 calls deepfakes as the “most serious AI crime threat”. It was published by the Dawes Centre for Future Crime at UCL.
The authors emphasized the fact that deepfakes, among other such manipulative content, would lead to a widespread distrust in video and audio materials online.
Professor Lewis Griffin of UCL said that “As the capabilities of AI-based technologies expand, so too has their potential for criminal exploitation. To adequately prepare for possible AI threats, we need to identify what these threats might be, and how they may impact our lives.”
They also accentuated the idea that AI crimes are highly repeatable and marketable. Criminal techniques could be copied and sold for money, as a service.
Does this remind you of anything? Indeed, the cybercrime-as-a-service phenomenon that’s been on the rise for some time now.
Here are a couple more AI-related cybersecurity risks:
I. Cyberattacks Optimization
Generative AI like ChatGPT is truly a force to be reckoned with, even in its premium form. Its research capabilities are nearly unmatched.
But did you know that it can be jailbroken? This means bypassing the restrictions imposed by the developers to control the AI’s answers to queries.
For instance, the regular ChatGPT will not engage in biased or racist replies and will also not provide information if it senses a malicious intent.
It won’t give you advice on how to commit a crime or build a bomb. But the jailbroken version of ChatGPT? The sky’s the limit. Or…the abyss.
A jailbroken LLM like ChatGPT can give you factual instructions on how to improve your malware or optimize your attack techniques.
It can teach you new social engineering manipulation techniques that you can implement on your victims.
Generative AI is good at one thing – doing the research for you and serving you the information in a digestible form in a fraction of the time it would take you to do it.
II. Automated Malware
Generative AI like ChatGPT is also good at coding, as it stands. It can not only write computer code but proofread it for errors and implement your ideas into code.
Now, what are most cyberattacks made of? That’s right, computer code. Normally, ChatGPT has protections against being asked to create malicious code for a cyberattack.
But through clever jailbreaking, those protections are made irrelevant and the true potential of ChatGPT becomes apparent.
Just this year, a Facepoint security researcher created an undetectable and super sophisticated data-stealing malware with ChatGPT.
He told ChatGPT what he needed and then he used the AI to construct the malware one line of code at a time. It was just him, a computer, and ChatGPT.
Here’s how the malware works:
- The malware takes the form of a screensaver app that auto-launches itself on Windows devices
- Once it reaches the device, it will start looking for data to steal
- It then breaks the data into smaller pieces and hides them within images on the device
- It uploads these images on a Google Drive folder to avoid detection
That’s all. The researcher was able to make the malware especially strong against detection with simple prompts.
He also claimed that he doesn’t have advanced programming knowledge and still, he managed to create a malware program on the level of nation-state malware.
Imagine what a full-fledged hacker would be able to do…
III. Physical Cyberattacks
Artificial Intelligence has infiltrated more and more into our lives – autonomous vehicles, AI-controlled medical systems, AI-controlled construction and manufacturing tools, etc.
While these are clearly technological advancements meant to make our lives easier, they also pose a significant cybersecurity risk.
Imagine that your autonomous car was infiltrated by a threat actor who manages to hijack the car’s operating system.
At that point, the hacker can effectively control all the car’s systems with you inside. They can drive the car, see through its cameras, use its GPS system, infiltrate other devices connected to it (like your phone), and more.
This isn’t at all theoretical, either. It has been done in 2015. Researches were able to hack into a Jeep Cherokee, access and control its radio, climate control, even the transmission, cutting off the driver’s access to the acceleration.
See, as technology advances, it brings with it good and bad uses. This doesn’t mean we should stop advancing as a society, but we should become much more aware of the malicious use-case scenarios of the technology we use.
Awareness through education becomes the central point of this discussion. We as a society should increase our cybersecurity awareness to avoid becoming cyber-victims.
To Conclude…
I won’t sugarcoat it – things are not looking good for us. Social engineering cases have multiplied rapidly in recent years.
Furthermore, several factors make matters worse for cybersecurity:
- Humans’ natural weakness against social engineering tactics and manipulation
- The emergence of the Cybercrime-as-a-Service phenomenon that trivializes cyberattacks, especially the Phishing-as-a-Service market that has expanded at a worrying pace
- The popularization of the work-from-home culture, which makes companies more vulnerable to cyberattacks due to a lack of streamlined cybersecurity control over employees’ devices
- The recent surge in Artificial Intelligence and Machine Learning capabilities, which opens up a host of new cyberattack methods and tactics
- The increase in state-sponsored social engineering attacks, which leads to more high-profile victims losing millions of dollars
But I’ll end this on a high-note.
Hope is definitely not lost yet. Artificial Intelligence and Machine Learning are also revolutionizing the cybersecurity industry as we speak.
By using AI’s pattern recognition capabilities and its prediction potential, cybersecurity tools will be able to assess and identify threats faster, more accurately, and more consistently.
Behavioral Biometrics is an entirely new industry that promises a revolutionary 2FA method for user protection.
Zero Trust Architecture is also evolving rapidly, gaining popularity among businesses and incorporating increasingly sophisticated security models.
Quantum Computing, while still in its infant developmental stage, promises to radically revolutionize the field of cybersecurity with its massively superior data processing capabilities.
But until these technologies materialize, the one thing we can start doing now to better protect ourselves is become aware of the risks.
Education is the best tool we have to stay ahead of the curve regarding our online security!
Sources
Statista – Share of Organizations Worldwide that Have Experienced a Loss of Sensitive Information as of February 2023, by Country
Statista – Percentage of CISOs in Agreement that Human Error Is Their Organizations’ Biggest Cyber Vulnerability Worldwide in 2023, by Country
Kaspersky – What Is Social Engineering?
Malwarebytes – Money Mules, If It Looks Too Good to Be True…
Trava Security – You Are the Weakest Link! (In Cybersecurity)
Harvard Business Review – The Neuroscience of Trust
Intuition – The Impact of the 6 Principles of Influence on Cybersecurity
Tripwire – Beyond the Firewall: How Social Engineers Use Psychology to Compromise Organizational Cybersecurity
Privacy Affairs – Why Is Phishing So Common & How to Protect Against It?
CNBC – Facebook and Google Were Victims of a $100 Million Dollar Phishing Scam: Fortune
Trend Micro – Austrian Aeronautics Company Loses Over €42 Million to BEC Scam
NY Times – A Brazen Online Attack Targets V.I.P. Twitter Users in a Bitcoin Scam
Phish Grid – Importance of Social Engineering Training for Employees – 2023
Fortinet – Spam Filtering
Threat Intelligence – Is MFA As Secure as It Used to Be?
Checkpoint – What Is Endpoint Protection?
Privacy Affairs – Cybersecurity Deep Dive: What Is the Principle of Least Privilege?
Privacy Affairs – Cybersecurity Deep Dive: What Is BYOD & 9 Security Risks
Privacy Affairs – What Is Cyber Insurance and How Does It Impact Cybercrime?
FBI – Business Email Compromises
Digital Guardian – Phishing, BEC Scams Netting $80,000 on Average in 2020
Forbes – Beware the Tactics Used for CEO Fraud by BEC Scammers
Statista – Distribution of Business E-Mail Compromise (BEC) Types in Worldwide Organizations from January to April 2023
Securance Consulting – State-Sponsored Attacks and What They Mean for Your Business
CSO Online – Protecting High-Value Research Data from Nation-State Attackers
Dark Reading – Microsoft: Ransomware & Nation-State Attacks Rise, Get More Sophisticated
Microsoft – Microsoft Report Shows Increasing Sophistication of Cyber Threats
Privacy Affairs – Cybersecurity Deep Dive: What Is Cybercrime-as-a-Service?
Cyren – 6 Phishing Techniques Driving Phishing-as-a-Service Operations
ZDNet – New Cybercrime Tool Can Build Phishing Pages in Real-Time
ABC News – “SIM Swap” Scams Netted $68 Million in 2021: FBI
Science Daily – “Deepfakes” Ranked as Most Serious AI Crime Threat
Malwarebytes – AI in Cyber Security: Risks of AI
Malwarebytes – Jailbreaking ChatGPT and Other Language Models While We Can
CBS News – These Jobs Are Most Likely to Be Replaced by Chatbots Like ChatGPT
Fox News – AI-Created Malware Sends Shockwaves Through Cybersecurity World
Wired – Hackers Remotely Kill a Jeep on the Highway—With Me in It
EC-Council University – Staying Ahead of the Curve: The Latest in Cybersecurity Technologies

