What is a VPN Concentrator and How does it Work?
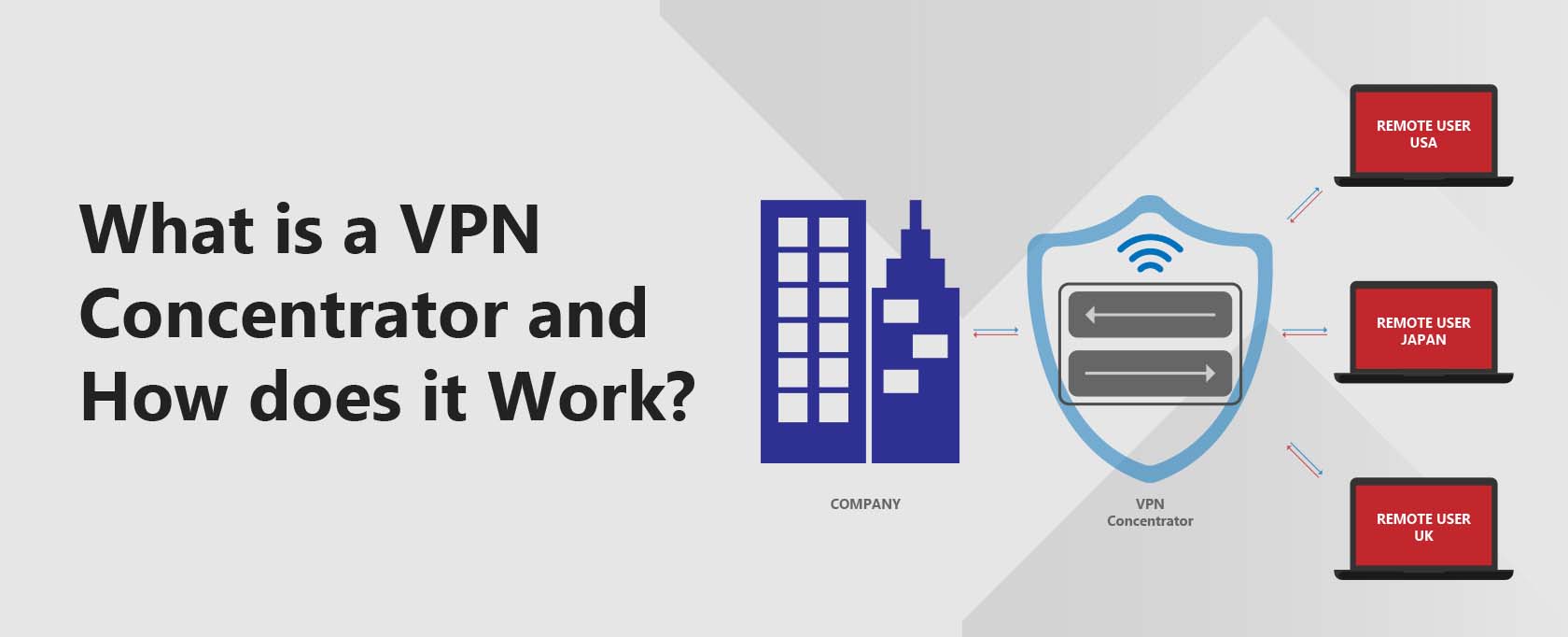
A VPN Concentrator is a networking device that enables multiple VPN tunnels to use a single network. VPN tunnels are secure connections that use advanced encryption techniques to protect information transmitted across the web. This ensures that data remains indecipherable even if intercepted.
VPN tunnels function independently from each other, and VPN Concentrators are specifically designed to manage VPN communications in secure multi-user environments.
They can create secure connections across TCP/IP networks, such as the Internet.
This allows users to maintain secure private connections over a public network without fearing that hackers will compromise their messages’ confidentiality.
VPN concentrators provide businesses and organizations with high-performance output, efficiency, productivity, and scalability. These devices can support thousands of users and offer secure private connections over public networks.
The article also covers the differences between VPN concentrators, VPN routers, site-to-site VPNs, and IPsec encryption, helping you assess which solution is best for your business needs.
Who uses a VPN Concentrator?
VPN concentrators are used by businesses and organizations that operate multiple systems connected using a network. This link might be a public network like the internet or a private network like a rented telephone line.
If the operators want their systems to be secure, VPNs will protect against any interception of their communications.
VPN concentrators can allow remote individual users to connect securely to a network using a VPN connection. They can also allow multiple users on one system to connect to various users on a second network by installing VPN concentrators.
What does a VPN Concentrator do?
VPN Concentrators use tunneling protocols to create and manage VPN tunnels. It receives incoming data, de-encapsulating and decrypting the data. It encapsulates the outgoing network data into encrypted packets and then transmits the data through the VPN tunnel.
A VPN Concentrator also manages user authentication and assigns users’ IP addresses. It also manages the cryptographic keys and handles network communications using standard VPN protocols.
In principle, VPN Concentrators act like a router but add an extra layer of security to the network traffic.
Why use a VPN Concentrator?
VPN concentrators provide a high-performance output, are very efficient and productive, and are expandable using Scalable Encryption Processing (SEP) modules. These enable users to increase the overall capacity and performance further.
VPN concentrators are capable of supporting thousands of users. VPN concentrators can operate at the heart of a small business with remote-access users connecting to the VPN network. They are also essential to corporations and organizations, handling more than 10,000 users effortlessly.
Key benefits of a VPN Concentrator
Users from anywhere in the world with access to the internet can securely connect with the business network. Their network traffic is being redirected and reshaped by the VPN Concentrator.
After the encryption process finishes, it sends the data and requests to the business server down an encrypted tunnel. The creation of the VPN tunnel usually occurs instantly on generating a communications request.
When you start up the software, it will automatically create a tunnel leading to the VPN concentrator so you can receive any data coming through it.
Software apps may be configurable to be Always-On, meaning that anytime you start up your device, it will always use an encrypted tunnel to connect to the corporate network via the VPN concentrator.
Hackers can infiltrate to plant malware or steal confidential data if a business doesn’t secure its networks. VPN concentrators provide security and encryption in these business settings.
While you might want to use a remote desktop app as a home user, especially if you’re working with a dynamic IP, this is not appropriate for business servers.
At the very least, they should have a VPN router working through the network. This has become a synonym with VPN concentrators because manufacturers are no longer producing standalone concentrators per se.
They incorporate the functions into multipurpose routers, which also include a firewall.
The VPN concentrator is a specialized router with more advanced protocols and algorithms. There are still regular routers available that you mustn’t confuse with a VPN concentrator.
VPN Concentrator vs VPN router
When choosing between a VPN concentrator and a VPN router capable of tunneling, you need to have all the facts. VPN routers vary depending on their underlying features, what kind of remote access you need, and what applications you will use.
The best VPN concentrators, on the other hand, are the type of devices that medium-to-large corporations use. They are industrial tools not aimed at individual home users. Also, they are considerably more expensive than ordinary routers.
Suppose you want your small company to benefit from added security with a lower financial investment. In that case, you should start with a VPN-capable router that acts as a gateway checkpoint for your server.
It will be harder to set up and configure than the concentrator because you will have to configure VPN clients on all remote devices in use manually.
A third option is a VPN appliance, which is more of a security multitool providing many advanced features but with weaker security than a VPN concentrator or VPN router.
VPN Concentrator vs Site-to-Site VPN
Site-to-site VPN connections are entirely different from concentrators. If you need to connect two or three sites, then Site-to-Site VPN is probably the best option.
This setup is ideal for fixed locations, such as a home office or satellite offices in other cities. The tunneling protocols offer access to the same databases and systems.
However, a VPN concentrator is the best option when you need tunneling protocols to provide remote access from random locations, mobile devices, or multiple users at once.
VPN Concentrator vs IPsec encryption
VPN concentrators generally use IPsec (Internet Protocol Security) or SSL (Secure Socket Layer) encryption protocols.
The SSL VPN uses the TCP port 443, and because most browsers also use SLL, this type of traffic matches the best with most networks. Port Forwarding can be used to customise the configuration.
This step enables the installation of SSL VPN clients into existing browsers or operating systems and allows access to employ user credentials. You don’t need additional IPsec tunneling because the SSL VPN functions on the browser, sending data back to the concentrator through the encrypted tunnel.
Using SSL VPNs eliminates the need to manually configure every end-to-end device and client software. However, some applications or software only allow IPsec VPN connections if you want to access the OS remotely.
IPsec will require separate client software to allow users to connect to the VPN tunnel. It has more configuration potential than the SSL-based VPN concentrators in terms of both local access and security levels.
However, correctly configuring IPsec client software running on the network through a concentrator is more complex and time-consuming.
Things get a little more complicated with mobile networks or remote laptop use. Some connection points might completely block off IPsec traffic, as is the case with many Wi-Fi hotspots.
- Transport mode – the data is encrypted. With the IPsec header and the IPsec trailer established on either side of the data, you use the original IP header to get the data to the remote site
- Tunnel mode – the IP header and the data are encrypted. There are still the IPsec header and the IPsec trailer set up around the data, but this time, a completely different IP header is brought forward at the front of the data packet. This way, anyone who intercepts the data will have no idea where it’s headed.
Conclusions
Before starting, you should assess whether your business needs a site-to-site VPN, a VPN router, or a VPN concentrator.
Many different solutions are available to secure your networks with reliable encryption and protect them from any external attack. The VPN concentrator is just one of the options and is one of the most sophisticated security network tools available.
While VPN concentrators produced by the large vendors support both SSL VPNs and IPsec VPNs, the lower budget devices tend only to keep one of these protocols.
Some apps will not work through an SSL-VPN client. Also, some SSL-VPN solutions may not support centralized storage or shared access to resources such as printers. Which protocol you should use will depend on your specific requirements.
IPsec VPNs offer the best options and generally provide more robust security than SSL-based VPNs. Also, the SSL-VPN concentrator will be simpler to configure and manage, decreasing the risk of misconfiguration causing security weaknesses.
Frequently Asked Questions
Some people found answers to these questions helpful
Is a VPN concentrator the same as a VPN router?
A VPN concentrator works similarly to a VPN router but has some differences. Think of a VPN concentrator as an advanced router. The significant differences include a VPN concentrator supporting thousands of simultaneous connections, authenticating users, and upscaling without impacting performance.
Who needs a VPN Concentrator?
A VPN concentrator is ideal for corporations with thousands of remote employees. It offers scalable simultaneous connections while ensuring employees connect securely to the major business network. Expanding a business can also benefit significantly from a VPN concentrator.
Are VPN concentrators similar to site-to-site VPNs?
Not really, although they may work in a somewhat similar way. A site-to-site VPN connects several sites in fixed locations. It is ideal as it eliminates configuring multiple routers. On the other hand, a VPN concentrator can connect numerous users from random locations.
What are some of the best VPN Concentrators?
The best VPN concentrator for your company depends on your needs, company size, and other value-added features. Popular reputable VPN concentrators include Cisco Meraki from Cisco, Short Tel, and Aruba from the Hewlett Packard Enterprise company. Shortel allows you to configure a remote IP telephony network.