Zero Trust Network Access (ZTNA): A Complete Guide
The Zero-Trust Network Access is an emerging security model which has received wider attention lately.
It enhances network security by enforcing strict identity and integrity verification for everyone who accesses networks.
Microsegmentation, Multifactor Authentication, Device Verification, Least Access Privileges, and Continuous Network monitoring are the core principles that comprise this model.
After thoroughly evaluating their current security posture and identifying the protection surface, organizations can transition into ZTNA by implementing the core principles.
Once ZTNA is in place, it provides many benefits besides using a good VPN and other traditional security models.
In this complete guide, you will learn about:
- What is Zero Trust Network Access (ZTNA)?
- How does ZTNA work?
- What are the principles behind ZTNA?
- How to Implement ZTNA?
- Types of ZTNA solutions
- ZTNA Vs. VPNs
- Benefits of ZTNA
ZTNA is built on key principles such as Microsegmentation, Multifactor Authentication, Device Verification, granting Minimum Necessary Access, and Continuous Network Monitoring.
I’ll walk you through the steps to adopt ZTNA, starting with assessing your current security measures and gradually integrating these essential principles.
ZTNA has many advantages over traditional security methods like VPNs. It secures remote workforce access, enhances data protection, improves user experience, and provides comprehensive network visibility.
What is Zero Trust Network Access?
In today’s world, where online working and learning have become the norm, there is a growth in the number of devices connecting to private networks both within and outside their perimeters.
As a result, networks have become more vulnerable to cyberattacks than ever before. The Zero-Trust Network Access model has come into the arena to mitigate this issue, and most companies are now transitioning toward it.
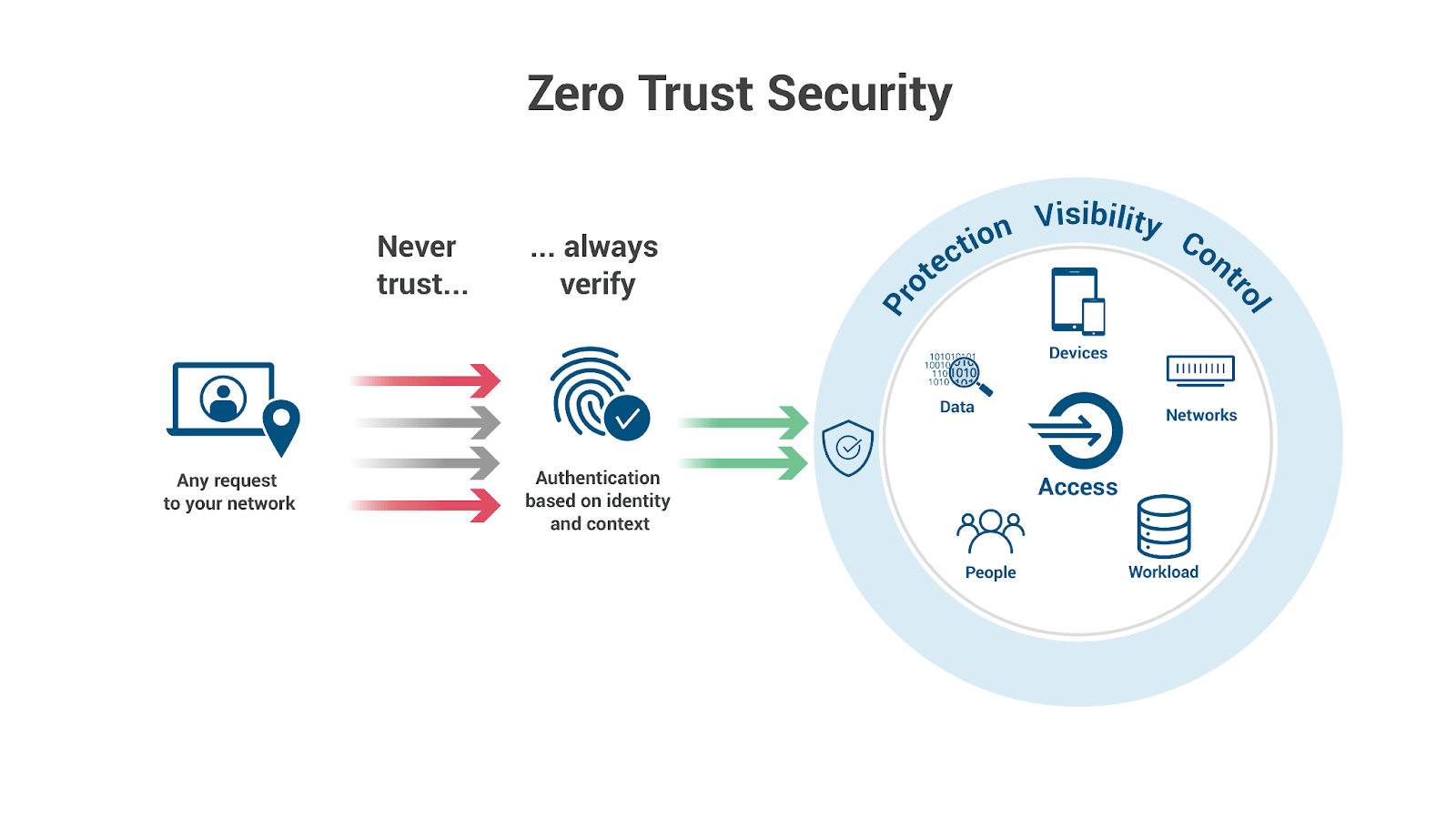
The Zero-Trust Network Access is an advanced security model that operates on the fundamental principle: trust no one – verify everything.
In other words, no user or device trying to gain access to a network, regardless of their location, will ever trust until they are entirely verified based on the established identity and access control policies.
Traditional Security Models Vs. Zero Trust Network Access
Because, typically, in security models like the ‘moat and castle,’ the devices connected within the network boundary have rights to access internal applications by default over the devices connected outside its perimeter.
Also, some networks grant access if the user is previously identified. Consequently, traditional security models overlook the security vulnerabilities caused by the users inside its perimeter because once a hacker gets inside the network, they have minimal resistance to hacking into internal applications.
The Zero trust networks overcome this weakness by providing an additional layer of security for your networks. In simple terms, they do not trust you by default but require you to undergo strict identity verification no matter where you access the network.
The ZTNA provides access to the applications and resources in the network only if you have explicitly granted permission.
In the Zero Trust Network (ZTNA) model, there is no such thing as a trusted user. Instead, it takes authentication as the fundamental principle and works under the following assumptions.
- Assume any user or device connected to the network and requesting access are hostile
- There exist threats to the network both internally and externally
- Every device and user should pass authentication and authorization
- Network policies should not be central to the whole network, but they should be dynamic and specific to each component.
Source: Zscaler
How does Zero Trust Network Access or ZTNA work?
First introduced by the Forrester Research firm in 2010, this model is not one single technology, but it consists of several principles unifying working together.
Similar to the characteristics of Software Defined Perimeters (SDP), In ZTNA, the applications and services hosted in the network are kept hidden from the users who do not have permission to access them.
The ZTNA service or the trust broker will authenticate the user and access the applications through an encrypted tunnel.
Principles of ZTNA
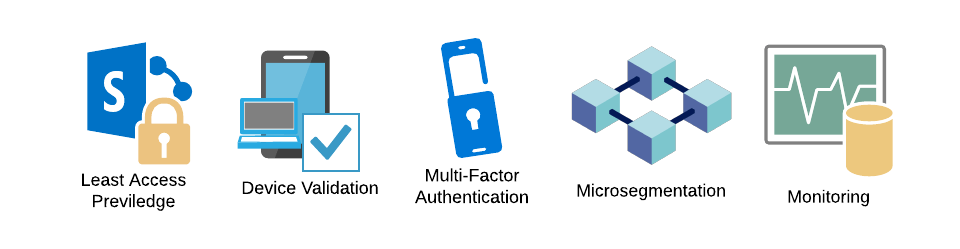
Let’s see the core principles governing this advanced technology that outperform traditional security models. The ZTNA operates on several security principles: Principle of Least Privilege (POLP), Micro-Segmentation, Multi-Factor Authentication (MFA), and Monitoring.
Least Privilege Access
This principle means any users will grant the minimum level of access or permissions they need to carry out their job successfully and not more than that.
So the user will not have access to the rest of the resources, and it will prevent the exposure of sensitive data and assets to everyone in the network.
This principle applies to humans and extends to non-human tools such as applications and connected devices that need access permissions to perform specific tasks.
Device Validation
Validate device health at all times by ensuring they meet the minimum health condition to access resources in the network. For example, in the Microsoft Zero Trust model, both Microsoft-owned and personal devices get enrolled into a device-management system controlled by health policies.
Multi-Factor Authentication (MFA)
MFA enforces users in a network to provide at least two pieces of evidence to prove their identity before gaining access to their accounts. It is a robust identity verification method that eliminates unauthorized access.
For example, you must provide a password to access accounts in a banking network. In addition, you may require a security code they sent to your registered mobile phone or email address so that they know accurately if it is you trying to gain access to their systems.
Most of the time, MFA provides Single-Sign-On capability allowing users to access multiple applications quickly.
Micro-segmentation
Microsegmentation is another key principle imperative to the ZTNA model. A security approach divides the network into multiple zones, defining fine-grained and flexible security policies for distinct network segments.
Furthermore, this approach provides the ability to define application-level security controls.
As a result, it mitigates the attackers’ lateral movements within the network even after gaining access inside the network perimeter because of the different security policies in various segments; the infiltration into every component is difficult.
Monitoring Everything
Continuous monitoring of network activity, including inspecting who and what devices are accessing the network, the access frequency, and behavior of each, is another security mechanism in ZTNA.
Zero Trust Network Access leverages intelligent analytics tools to help monitor what is happening with your network in real-time.
Monitoring enables you to identify abnormal behaviors and notify and warn potential attackers that they are being monitored and denied access to the network.
How to Implement Zero Trust?
Implementing ZTNA in a legacy network is not straightforward, but it is an iterative process that involves a series of decisions and actions. This section will discuss the general steps you can follow in moving towards the ZTNA model.
1. Identify all the assets and define the protection surface
The first step towards implementing the ZTNA model is identifying all the data, assets, applications, and services, including:
- Sensitive data
- Computers and laptops
- Mobile devices
- IoT devices
- Employee Personal Devices
- Client devices
- Software and applications
- User accounts
- Virtual resources
Maintain a catalog of devices and data, which part of the segment they lie in, and which users require access. Performing this step can isolate the protection surface the ZTNA needs to be in place.
Depending on sensitive data locations, it can be either the whole network or only a part of the network.
2. Understand your organizations’ current security posture
Assess your current security environment, policies, and procedures and get a good grip on where your overall security posture stands now. This step is a form of the gap analysis phase.
You can identify what security glitches exist within your environment and where you are currently getting into the ZTNA model.
3. Mapping transaction flows
Analyze how sensitive information flows within your network, which is imperative in identifying dependencies between network segments. Map out and document your traffic flows so that you can get insights on how users access data, in which parts of the networks they flow interdependencies with devices and networks.
In addition, it helps define controls over specific traffic flows to ensure only permitted traffic flows within the network.
4. Design the Zero-Trust-Network Architecture
Once you have identified your sensitive data and protection surface, mapped out traffic flows, and performed the gap analysis, you are equipped with the necessary knowledge to build your ZTNA architecture.
In this phase, if your company does not have the required expertise for ZTNA, you can get the help of a third-party ZTNA expert or a service provider to design the architecture that best matches your needs.
5. Implement Zero Trust Network Access (ZTNA) principles
The next is implementing the security principles we discussed above. Next, execute the micro-segmentation creating granular network zones and enforce specific security policies for each segment.
During this process, place next-generation firewalls as segmentation gateways for application-level packet inspection beyond protocol inspection. In addition, implement the multi-factor authentication mechanisms if your organization doesn’t have them.
6. Monitor the network
As the final step in achieving Zero Trust, you can monitor traffic logs and understand how your network improves over time with the Zero Trust model. Once you have gone through these steps for the first time, you can expand them further.
Types of Zero Trust Network Solutions
According to Gartner, there are two main categories of ZTNA solutions.
Endpoint-Initiated Zero Trust Network Access
In this solution, end-user devices have installed agent software to collect information about the devices’ security status and transmit that information to a controller.
Next, the controller requests authentication from the device and sends a list of allowed applications. Upon successful authentication, the controller permits the device to connect to the requested application via a gateway.
Service-Initiated Zero Trust Network Access
Unlike Endpoint initiated ZTNA, this solution does not require installing an agent, but applications have a connector to establish outbound connections.
If you want to access the application, you must pass the authentication with the ZTNA provider, who validates the users using the Identity Access Management mechanism. After successful verification, the traffic can pass the provider.
It will be helpful for devices that are difficult to install the agents.
ZTNA Vs. VPNs
VPNs have been used for many decades and are still the most widely used method to access corporate networks remotely.
However, with the growth of remote working and learning, many companies have identified the shortcoming of using VPNs over the emerging technology of Zero Trust Network Access (ZTNA).
Security – Once remote users are connected via VPN, they have full network access because VPNs assume that any user who gains access through the VPN can be trusted.
If the user device contains malware, it will be exposed to cyber-attacks. Therefore, the networks are more exposed to security threats with VPNs. However, unlike VPNs, ZTNA is more secure as it provides user-based access control, never trusting a user until fully verified.
User Experience – VPNs have limited simultaneous VPN connections and are limited to one particular location at a time.
In addition, you need to install a VPN, which some users may find a difficult task. Moreover, VPNs can slow your connection speed. But on the other hand, Zero Trust Network Access users can stay connected to the network.
This is because it does all the necessary operations behind the scenes.
If you need to choose a VPN then check out our best VPNs roundup.
How ZTNA improves Business and Security?
1. Protect the remote workforce – Firewalls and VPNs no longer provide the necessary security for ever-increasing user connectivities.
But with Zero Trust enforced security principles, users guarantee that their connection undergoes additional layers of protection, providing a sense of assurance that they are safe under Zero Trust Network Access.
2. Improve Data Protection – Traditional security models are highly vulnerable to data breaches. If a data breach occurs, companies have to face serious consequences, such as GDPR fines.
It will incur additional costs and cause reputational damage. The ZTNA models assume that everything inside and outside the network is hostile. Therefore, everything is protected with different security principles to safeguard your data as much as possible.
3. Improve the User Experience – Simple and easy-to-use MFA and Single-Sign-On capability provides less complex access without remembering multiple passwords for multiple accounts.
4. Gain visibility into the network – Once you have set up monitoring, you can monitor all your resources and network activity.
You’ll have complete visibility into who and what accesses your network. Thus you will have all the information like the time, location, and devices that made the request.
Wrap Up
In conclusion, ZTNA provides advanced security to enterprise networks by enforcing several security principles. In addition, it provides an additional security layer to traditional remote access methods like VPNs.
Because of its business and security benefits, organizations tend to move to this model.
Frequently Asked Questions
Some people found answers to these questions helpful
How does ZTNA work?
Zero trust security operates on the principle that trusting no one by default, even inside the network perimeter, requires verification for anyone trying to gain access to resources on the network.
What are the challenges of achieving ZTNA?
If the organization is well-established, re-organizing the current network will take time and effort. Implementing a new network from scratch will be easier, but the costs associated with it could be unbearable. Also, moving legacy system users and managing access to different types of users and devices can be complex and time-consuming.
Is ZTNA part of SASE?
ZTNA is part of SASE or Secure Access Service Edge, which offers effective guidance in designing security solutions. It comprises various security services, including ZTNA, NGFW, and other security and network services.
What is the most popular ZTNA software?
Okta, Perimeter 81, Duo Security, Twingate ZTNA software, and Zscaler Private Access are among the ZTNA software on the market.



2 Comments
Barry
May 2, 2022 8:19 pm
Great article Shanika. Not sure you realized that the first graphic you used titled “Zero Trust Security” is from Cloudflare’s learning center article. Glad you liked it to use it. It’d be awesome if you included Cloudflare Zero Trust as one of the popular ZTNA services available.
https://www.cloudflare.com/products/zero-trust/
Miklos Zoltan
May 5, 2022 8:36 am
Hey Barry. Thanks for bringing this to our attention! Yes, absolutely, I’ll make some edits soon to credit the image as well as mention Cloudflare Zero Trust.